Security
3 reasons DDoS attacks will get worse in 2017
If you think 2016 was filled with ridiculous DDoS attacks, wait until what 2017 has in store for us. Here’s why.
Just a heads up, if you buy something through our links, we may get a small share of the sale. It’s one of the ways we keep the lights on here. Click here for more.
So, what gifts did you receive for the holidays? If you are a techie, you may have gotten a new smartphone or tablet; or perhaps you received a DVR or a faster Wi-Fi router to connect all your Internet of Things (IoT) devices.
But as the number of internet-connecting machines grows, so do the risks. Did you know that hackers and cybercriminals regularly recruit user devices through Trojan horse programs and malware downloads? Your computer could be infected without you even realizing it. Digital deviants can create large networks of ‘slave’ or ‘zombie’ computers in what is known as a botnet, which can then be used to flood businesses or websites with excessive traffic requests until the service crashes, costing big bucks in business losses. This is what is known as a Distributed Denial of Service, or DDoS, attack.
Following several high-profile incidents this year, DDoS has nearly become a household word. But experts say that the worst is yet to come. As we wrap up 2016, it’s important to look to the new year to see how we can mitigate the growing threat of DDoS disasters.
IoT Hits the Fan
DDoS, admittedly, isn’t a new problem. Hackers have been flooding websites with phony traffic as part of internet protests and disruption attacks since the early 2000s. And the vast majority (93 percent) of DDoS attacks are relatively small, lasting around 30 minutes. Still, this is nothing to scoff at as these attacks can frustrate customers, decrease revenue and be used as a distraction for a greater attack (see below).
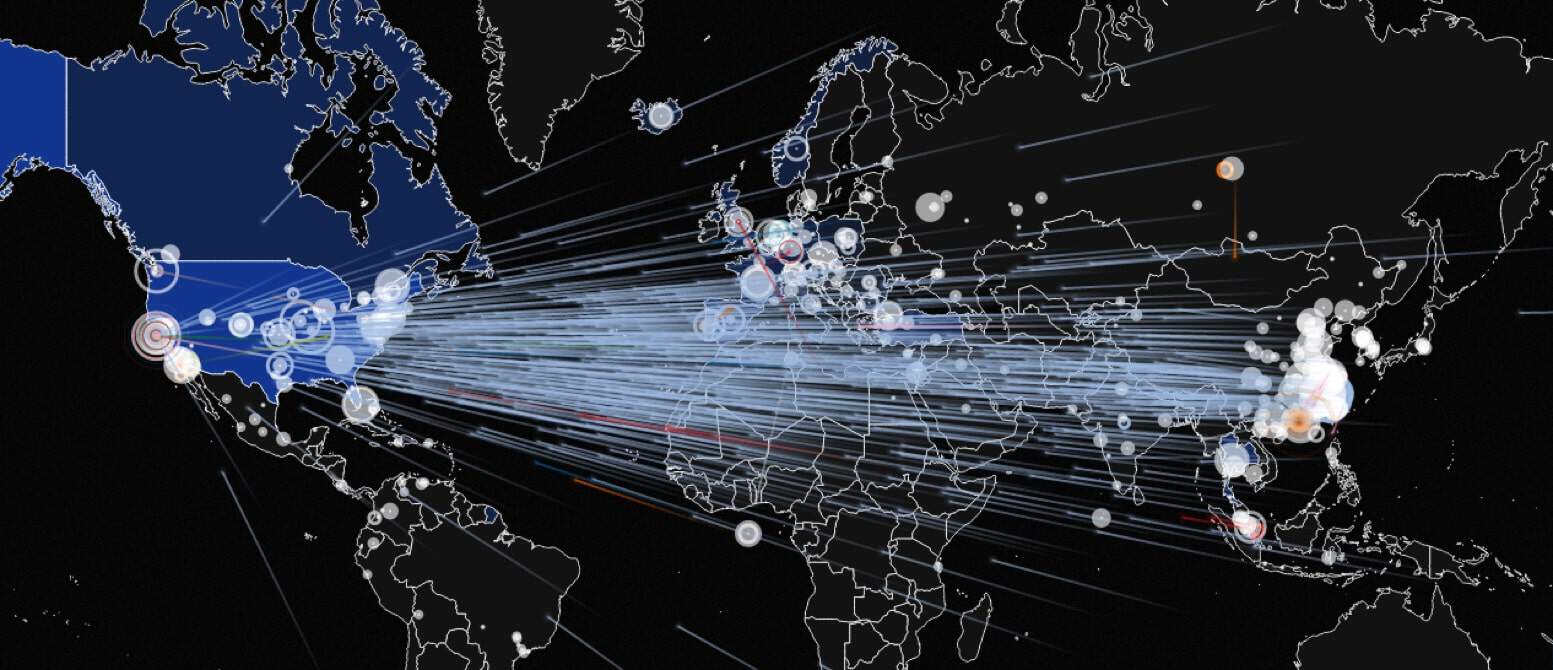
However, with recent events it looks as if large-scale attacks are on their way. In January 2016, Dark Reading correctly predicted that a growing number of notoriously unsecured IoT devices would bring about large-scale DDoS attacks, dubbing it the burgeoning “Botnet of Things.” The Mirai botnet fulfilled the prophesy.
Mirai is largely made up of cracked DVRs, webcams and routers. While it’s big debut in September crashed Krebs on Security and French webhost OVH, it’s real showstopper took place on October 21, when it crashed the popular Dyn DNS, resulting in crashes to some of the world’s top sites including Amazon, Netflix, Paypal and Twitter.
For comparison, a regular 30-minute DDoS attack runs about 1Gbps in size, the Mirai botnet ran at 620Gbps and now the Leet Botnet might be taking the lead with 650 Gbps! You don’t need to be a tech genius to know that this is a big problem; and things will only get worse as more devices come online!
Extort, Distract & Conquer
At its core, DDoS is a business disruption tool meant to crash operations and slow servers; but crafty cyber crooks won’t stop there. Hackers will sometime use a small DDoS attack to distract administrative and IT teams searching for a solution, while the hackers pilfer data or install malware programs on the company’s network. Attacks of this nature are especially hard to detect unless you have proper visibility over your network and a deep understanding of how subsequent attacks are cloaked.
Similarly, hackers will sometimes employ a form of extortion in which they flood your network with a steady stream of phony web requests until you pay up — on the surface, this is not dissimilar to a ransomware attack, except that it happens on the network level instead of the software level and hackers do not need to infiltrate your network to do damage.
DDoS as a Service
To make matters worse, “DDoS for hire” is now being marketed on the dark web as “network stress testers” (although they don’t really care what you’re testing). This means that for a few dollars an hour, anybody can take control of a massive botnet and stymie legitimate web traffic from reaching your site — no tech expertise necessary.
Think about it: a disgruntled employee, a novice hacker, a black hat extortionist… anyone could inflict serious damage to your company for any reason. What are you going to do about it?
Thankfully, there are several DDoS protection strategies to safeguard your business against cybercriminals. The first is to prevent your devices from malware recruitment. Be sure to replace the default settings on all your devices immediately with a strong passphrase. This will bar brute force attacks which can easily decode commonly used factory settings to infiltrate your device.
Next, consider investing in DDoS protection techniques from an in-house IT team or reputable provider. Part of DDoS protection is understanding and differentiating legitimate user behavior from that of bots or hackers. This way providers can detect malicious traffic before it causes problems by redirecting it to a null interface where it can do no damage (known as ‘sinkholing’) or blocking it entirely with a firewall or front-end application.
If 2016 really was the Year of the Botnet, let’s be sure 2017 is the Year of Cybersecurity!