News
Hackers have been utilizing an insanely clever tactic to break into your email account
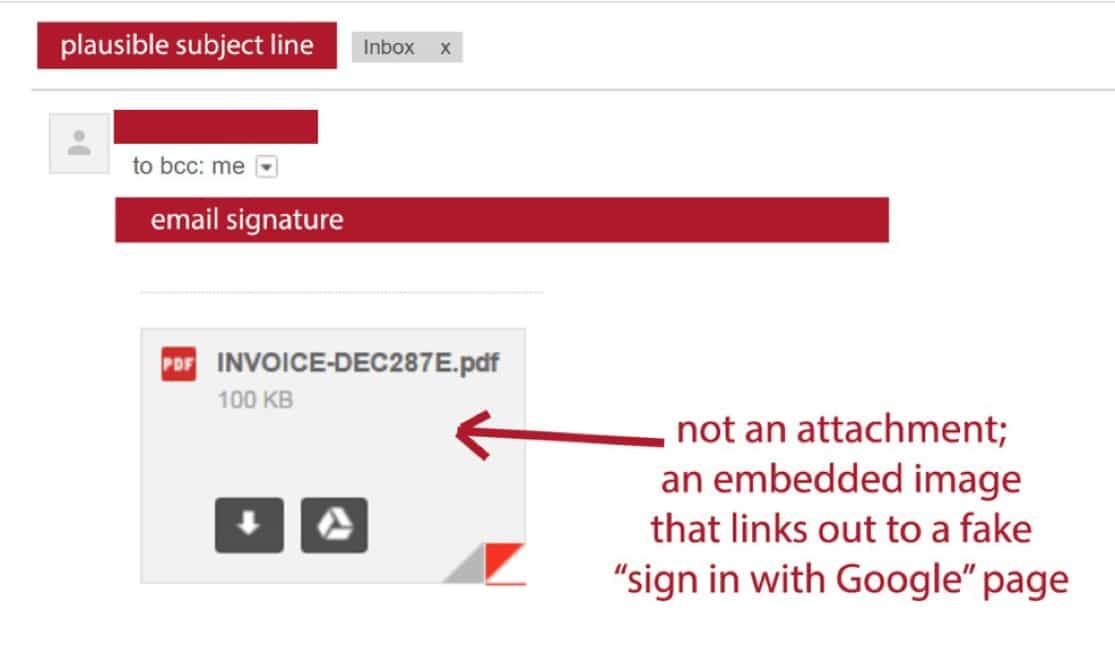
There’s a nasty email scam going around that utilizes a believable subject line by someone you know along with a infected PDF file.
Just a heads up, if you buy something through our links, we may get a small share of the sale. It’s one of the ways we keep the lights on here. Click here for more.
There’s a nasty email scam going around that utilizes a believable subject line by someone you know along with an infected PDF file.
If you one of your friends or contacts recently emailed you with an attached PDF file, be careful, it may be a targeted email scam.
That’s right, a shady email scam is making its rounds in hopes it tricks an unsuspecting user to give up their login credentials by “sending over a (fake) link to a PDF to open,” Business Insider reports. The worst part? The email is sent from an email that’s also been compromised and uses highly-popular subject lines that gets you to click on them.
Here’s how Business Insider breaks down how it works:
- The attacker, using a compromised email account, sends emails to that first victim’s contacts.
- The email contains what appears to be a link to an attachment (often a PDF) hosted on Google Drive.
- This lowers the target’s defences, because they can — in theory — view documents on Google Drive without having to download anything.
- If the would-be victim clicks the link, they’ll be directed to a page masquerading as the Google login page.
- They enter their login details when prompted — and just like that, the hacker has access to their account!
- The attacker then starts the process all over again, targeting the most recent victim’s contacts.
Here’s what’s scary – “the email isn’t just some generic template. It often actually borrows the subject line and (fake) file name from previous correspondence with the person being targeted, making it seem super plausible,” Business Insider further reports.
Here’s how one user from the discussion site Hacker News describes his experience at his workplace:
“They went into one student’s account, pulled an attachment with an athletic team practice schedule, generated the screenshot, and then paired that with a subject line that was tangentially related, and emailed it to the other members of the athletic team.”
The school was “hit by this hard right before the holiday break,” they wrote. “Three employees and a handful of students all got hit by the attack within a two hour period. It’s the most sophisticated attack I’ve seen.”
Apparently, this email scam has been going around for a while. Here’s a a blog post on Gregmann.com in 2016 that details how the author fell for it after he was emailed with it:
“Only after it failed and didn’t ask for my 2 factor authentication I realized I had just been phished. I immediately changed my Google password. Fortunately my google password is not used on any of my other accounts,” he wrote. “It’s so scary that it was so easy to fool me. I’d guess most non-techies would fall for this too and most non-techies don’t have 2 factor on so they’d have been owned immediately.”
The solution? Use different passwords for everything and make sure they’re strong. That means capitalize letters, use numbers and special characters. Most importantly, enable two-factor authentication if possible. Protect yourself because if you don’t, you will get hacked. The proof is everywhere.