Sponsored
How to implement zero trust security in your cloud-native environment
This article aims to educate people about zero trust security’s value in cloud native environments and cybersecurity threats.
Just a heads up, if you buy something through our links, we may get a small share of the sale. It’s one of the ways we keep the lights on here. Click here for more.
Disclosure: This is a sponsored post. However, our opinions, reviews, and other editorial content are not influenced by the sponsorship and remain objective.
The idea of “never trust, always verify” underpins the concept of Zero Trust. Originally, the concept of granting access was to give everyone unrestricted access to resources and to do so while presuming that everything on the network is secure.
In contrast, companies should only allow access to resources to those with a legitimate need for them and only after confirming the requestor’s identity and security posture when we talk about zero trust.
With this strategy, all requests for access to a network or any application running on it are merely viewed as potentially harmful.
To safeguard resources, security measures must be implemented to verify requests and user identities before access is granted.
Assuming that an attacker may already be in the network, zero trust security requires all requests to be authenticated and approved before being granted access.
Cloud-native environments must implement zero trust security due to the complex and dynamic nature of cloud systems.
Because applications and services are spread across cloud providers and data centers, it’s hard to track who’s using what, where, and how.
Zero trust security can help companies control user access to cloud resources and reduce security risks.
Cloud-native security challenges

Implementing zero-trust security in cloud-native environments requires a holistic approach considering the unique security challenges presented by microservices, APIs, and container orchestration.
This involves implementing identity and access management (IAM) controls, network segmentation, encryption, and monitoring and logging at every layer of the cloud-native stack to ensure proper cloud native security.
It also requires a shift in mindset from assuming that all traffic within the network is trusted to verifying and validating every request and user before granting access.
By adopting a zero-trust approach, organizations can improve their security posture and reduce the risk of a data breach or other security incident.
Microservices in a cloud-native environment are deployed independently and are very distributed in nature.
Due to this distributed nature of microservices, controlling access and monitoring those microservices is the biggest hurdle when implementing zero trust.
These problems are adequately addressed by a zero-trust security approach, which uses capabilities like IAM, network segmentation, encryption, monitoring, and logging.
These services provide granular identity and access controls at every layer of the cloud-native stack.Zero trust security can help organizations control cloud native resource access and reduce security risks.
By validating users and requests, organizations may ensure that only authorized users have access to the resources they need to do their tasks and that any unauthorized or suspicious behavior is detected and blocked.
Zero Trust Security Framework
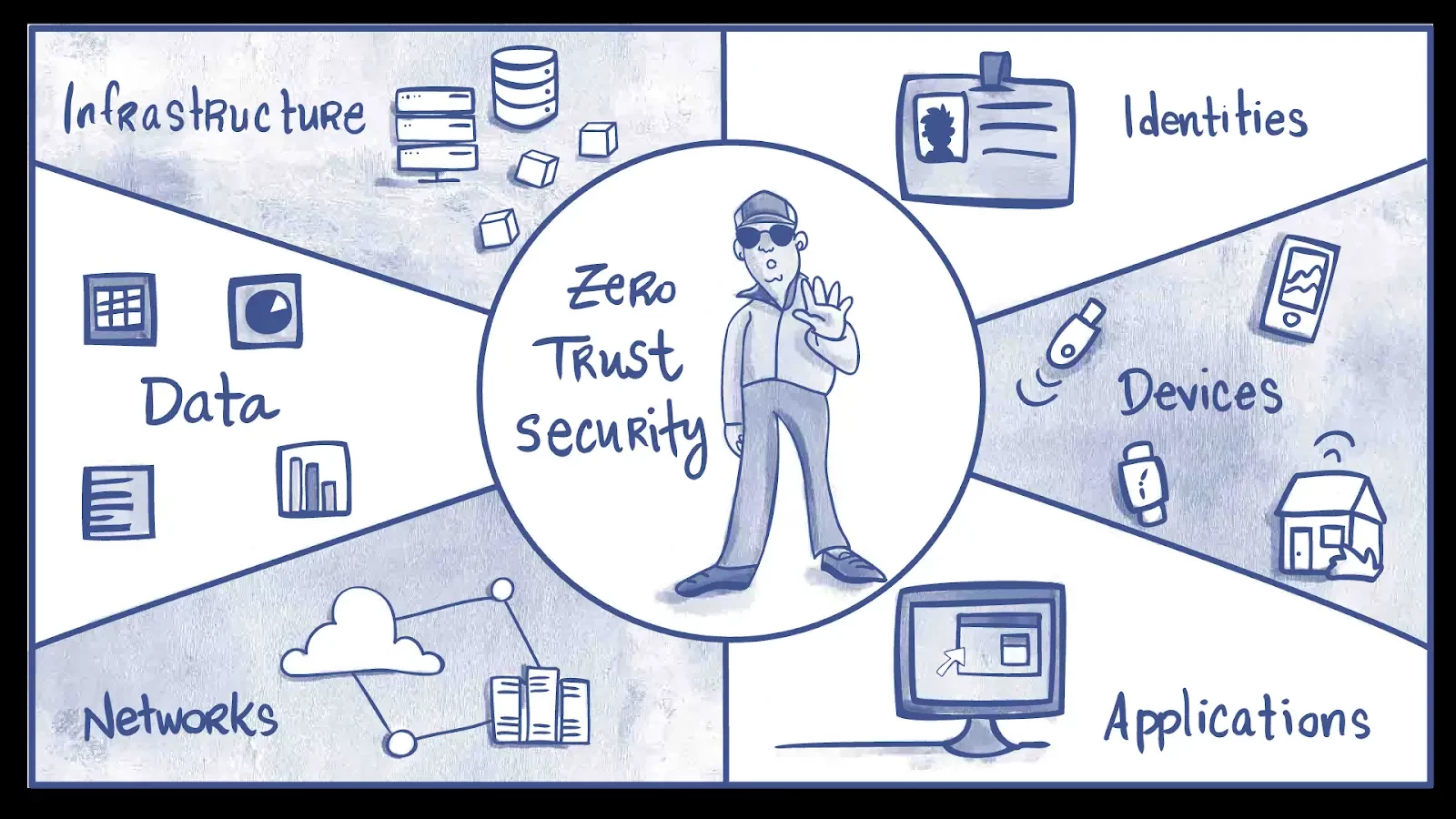
“Verify explicitly” is a zero-trust security framework principle. This principle states that any user or device seeking access to resources must first be expressly authenticated and validated as legitimate.
Also, it follows the idea of least privileges, which asserts that users should only be given the access they need to do their duties.
Another principle is constant monitoring, which requires network observation for risky or suspicious activity.
Implementing Zero Trust in a cloud-native environment involves adding a powerful IAM solution that enables centralized control to be built over users and devices.
They perform micro-network segmentation to implement strict access controls and reduce the attack surface.
This also entails carrying out continuous monitoring and logging to be able to trigger alerts or incidents if something goes wrong.
Implementing Zero Trust Security in a cloud-native environment
Implementing zero trust in cloud-native environments is not easy.
Since all the resources are scattered in different geographical locations and might be using different microservices, we first need to identify all the resources before we can enforce policies or monitor those resources.
Identify and inventory cloud assets
You must identify and inventory all your cloud asses to achieve Zero Trust security in a cloud native environment.
This stage identifies all microservices, APIs, containers, and other cloud native resources, as well as the devices and people that use them.
A simple scanner like a prowler or scout suite can be used to check all of an organization’s services. To successfully implement Zero Trust security practices, the company must have a complete and up-to-date asset inventory.
Enforcing policies and monitoring
Implement access controls after inventorying cloud assets. User, device, and resource-specific least privilege access constraints are needed.
Access restrictions that are dynamic and granular are necessary for cloud-native environments. Completing a cloud-native zero-trust architecture also requires monitoring and verifying user access.
Security information and event management, intrusion detection, and log analysis enable continuous monitoring and verification.
Tools and technologies for Zero Trust Security
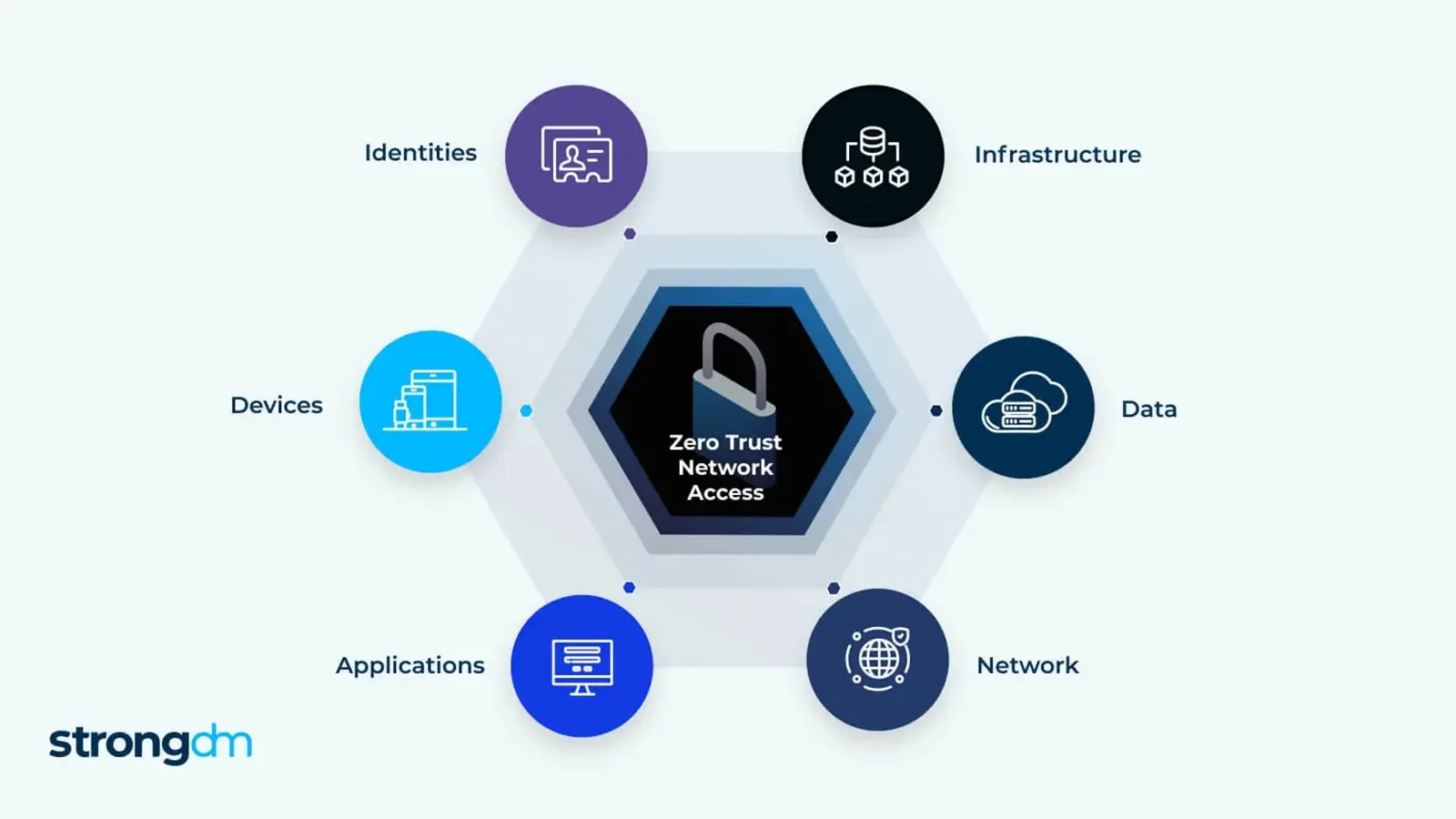
Zero trust involves tools and technologies that encrypt and manage resource access, monitor network activity, and detect and respond to threats in real-time.
Service meshes, which manage dispersed microservices securely, enforce zero trust. Istio is a popular zero-trust service mesh platform that can implement zero trust in distributed architectures.
Istio offers mutual TLS authentication, authorization, and encryption to protect service-to-service communication. Additionally, it uses load balancing, circuit breaking, and fault injection to govern service traffic.
Another tool, Calico, can also be used to implement zero-trust policies. Calico provides network policies, encryption, authentication, access control, and monitoring services.
With Calico, you can ensure that only authorized traffic is allowed within different parts of your network and that all communication is secure and private.
Additionally, you can detect and respond to security incidents quickly and effectively.
Best practices for Zero Trust Security in a cloud-native Environment
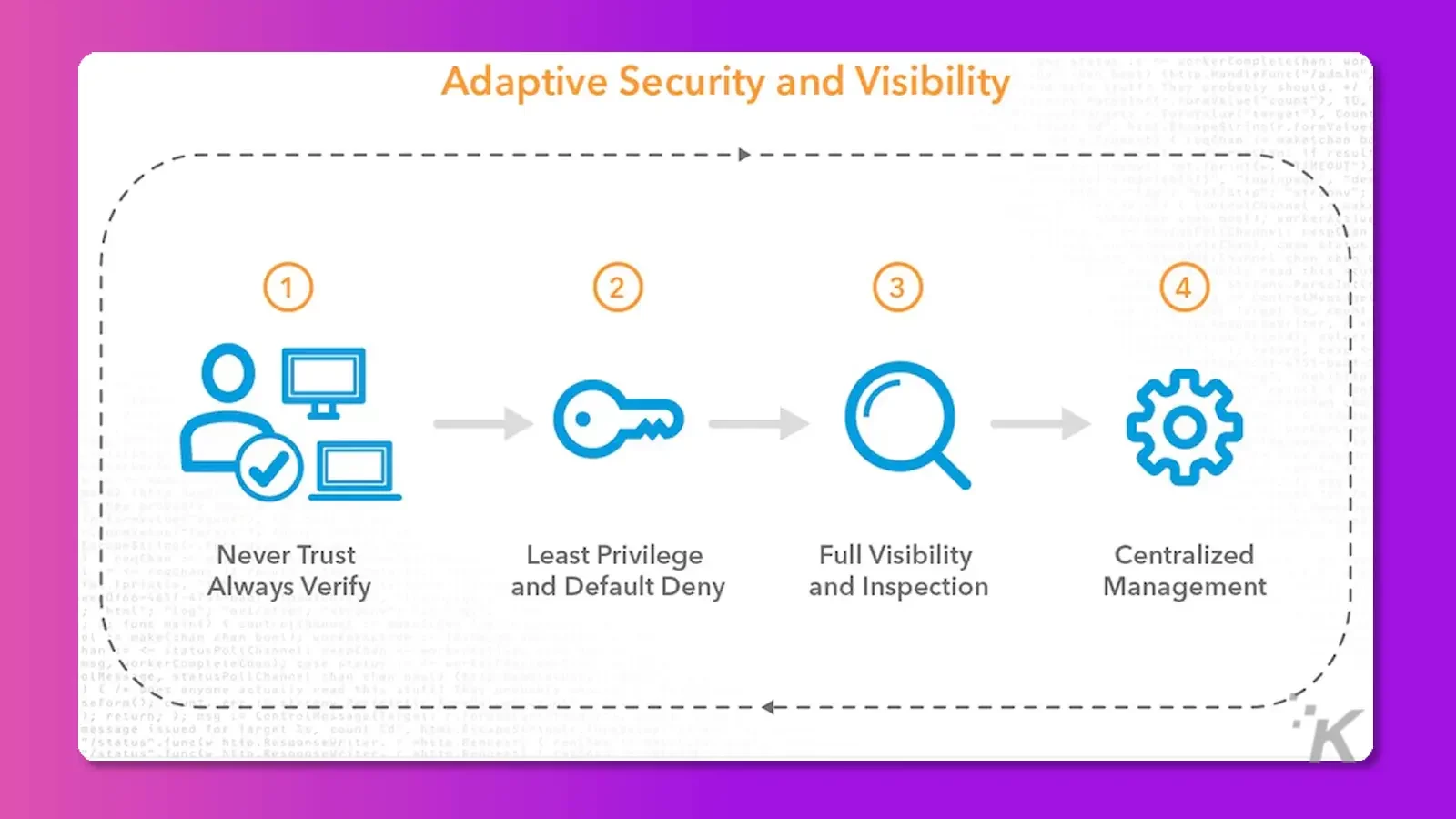
There are a lot of different best practices that can be used to implement and maintain a zero trust environment.
You can implement SSO with MFA, using AWS secrets managers to secure and save keys and sensitive assets and performing security monitoring of assets by implementing incident response programs. Let’s discuss these further.
Use of SSO with MFA
MFA and SSO can help ensure that only authorized users access sensitive data or applications in a zero-trust security model.
By requiring multiple forms of identification and using a centralized authentication mechanism, organizations can more effectively enforce zero-trust policies and protect their resources against unauthorized access.
Use of continuous security testing and monitoring
In zero trust, continuous security testing and monitoring can help organizations ensure that only authorized users and devices access sensitive data and applications.
By continuously testing for security vulnerabilities and monitoring for potential threats, organizations can reduce the risk of unauthorized access. Therefore, this ensures that their security policies are being enforced effectively.
Conclusion

In conclusion, implementing Zero Trust security in a cloud-native environment is critical to ensure the security of cloud assets and protect against potential security breaches.
This approach involves identifying and inventorying cloud assets, defining and enforcing granular access policies, and continuously monitoring and verifying access.
By following these steps, organizations can improve the security posture of their cloud-native environments and reduce the risk of a security breach.
However, it is important to remember that security threats constantly evolve, and new vulnerabilities emerge daily.
Therefore, it is essential to continuously assess and update security measures in response to new threats.
Moreover, this includes monitoring the cloud environment for new assets and access attempts and staying up-to-date with the latest security best practices and emerging threats.
By adopting a proactive and continuous approach to security, organizations can stay ahead of potential threats. Furthermore, ensuring the ongoing protection of their cloud-native assets.
Therefore, this article aims to educate people about zero trust security’s value in cloud-native environments. Cybersecurity threats require zero trust security.
Our significant experience in cyber security was invaluable in writing this piece. Through this discussion, we were able to impart both theoretical and practical knowledge on the topic of zero-trust security implementation.
We spent much time researching and drawing on our professional knowledge to ensure the content was useful, accurate, and up-to-date.
Have any thoughts on this? Drop us a line below in the comments, or carry the discussion over to our Twitter or Facebook.
Editors’ Recommendations:
- Cyber security tips for your business in 2023
- The importance of visibility in cyber security
- Businesses seek cover from growing cybersecurity threats
- The most important cybersecurity practices for your business
Disclosure: This is a sponsored post. However, our opinions, reviews, and other editorial content are not influenced by the sponsorship and remain objective.