Security
A new but old type of malware is now targeting Macs and it’s not pretty
If you think your Mac is safe from malware attacks, think again because security researchers just detected a new one this week.
Just a heads up, if you buy something through our links, we may get a small share of the sale. It’s one of the ways we keep the lights on here. Click here for more.
Remember when everyone thought Macs were impenetrable to viruses and malware? Well, times are a-changing because a recent report from security researchers claim one of the oldest kinds of Windows malware is now being targeted on Macs, reports Ars Technica.
Business Insider writes:
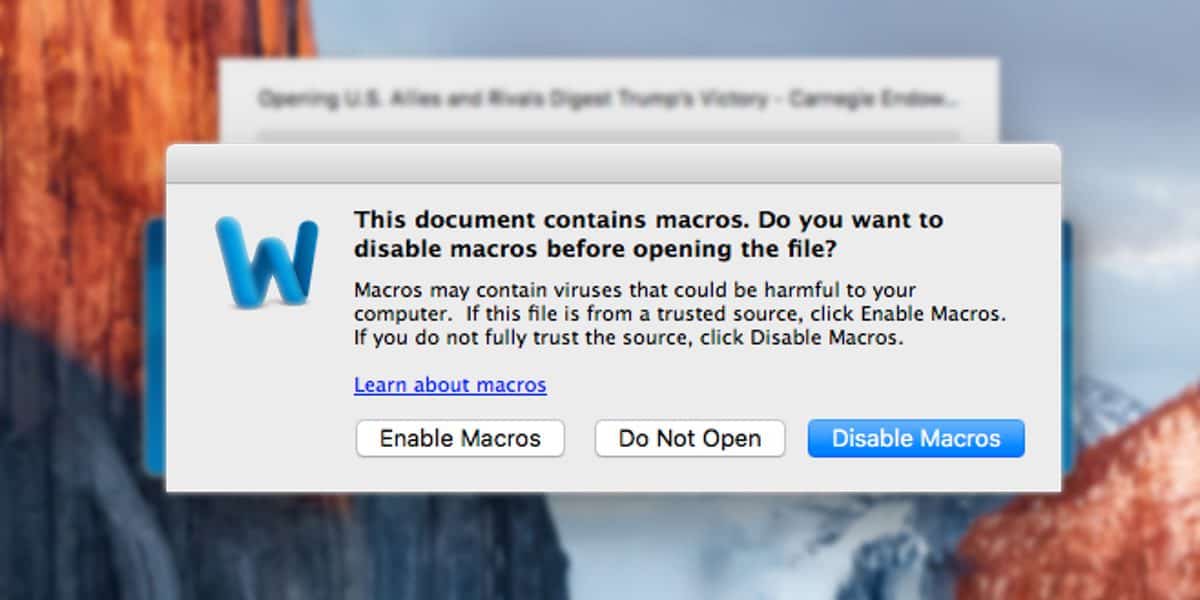
The attack used one of the oldest tricks in the Windows hacker’s book: taking advantage of Microsoft Word macros, or short bits of script that can be used to automate people’s work.
At least, that’s how macros are intended to be used. But malware makers can use them to download a malicious payload.
Researchers found a Word file called “U.S. Allies and Rivals Digest Trump’s Victory – Carnegie Endowment for International Peace” that contained a boobytrap that would download malicious code from a Russian address and run it on the victim’s computer.
Once the boobytrap runs, it can “perform a myriad of nefarious actions such as enabling the webcam, dumping the keychain, and accessing a user’s browser history,” according to security researchers.
Heres’s a little more analysis from the security researchers who first discovered the vicious malware:
“By using macros in Word documents, they are exploiting the weakest link; humans!” Patrick Wardle, who is director of research at security firm Synack, wrote in an analysis of the malicious document. “And moreover since macros are ‘legitimate’ functionality (vs. say a memory corruption vulnerability) the malware’s infection vector doesn’t have to worry about crashing the system nor being ‘patched’ out.”
Moral of the story here? Don’t open unknown Word documents from strangers. If you already have, these folks can offer some amazing support.
► Business Insider via Ars Technica