Apple
iMessage flaw may have enabled zero-click targeted attacks
Apple recommends that such high-risk users enable Lockdown Mode, which disables some features to reduce vulnerability to sophisticated attacks.
Just a heads up, if you buy something through our links, we may get a small share of the sale. It’s one of the ways we keep the lights on here. Click here for more.
A recent report from security firm iVerify has revealed a potential security issue in Apple’s iOS operating system that may have been used in highly targeted attacks on iPhones in the US and Europe.
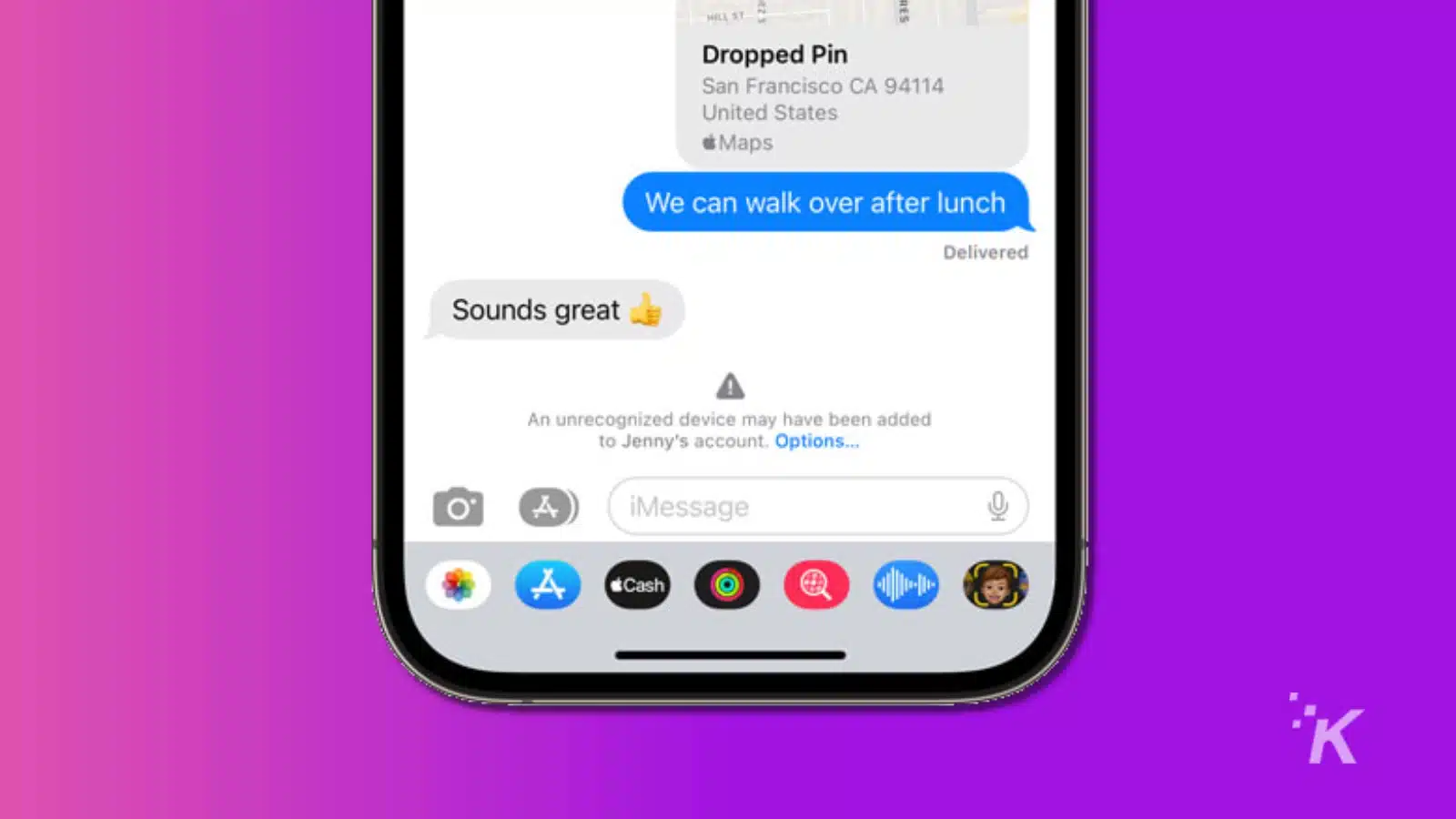
The flaw was found in a seemingly minor feature: the nickname update function in iMessage.
When someone updates their profile nickname, photo, or wallpaper, it sends a small data update called a Nickname Update to others they message.
While this sounds harmless, the update is automatically trusted by the system, and because it happens inside a secure part of the phone, it creates a new opportunity for attackers.
This vulnerability was present in versions of iOS up to 18.1.1, and Apple fixed it in version 18.3.1.
iVerify did not find concrete evidence that the flaw was actively exploited, but in their analysis of crash data from nearly 50,000 iPhones, a few rare cases stood out. (Via: Forbes)
These crashes occurred on phones belonging to individuals at high risk, such as people in political campaigns, media, tech companies, or government organizations in the US and EU.
Moreover, Apple recommends that such high-risk users enable Lockdown Mode, which disables some features to reduce vulnerability to sophisticated attacks.
It’s not clear whether Lockdown Mode would have blocked this issue, but since the flaw is now patched, the risk is resolved for updated devices.
Both iVerify and Apple agree that iOS is still a secure platform, and the popularity of iMessage makes it an attractive target, not necessarily a weak one.
However, iVerify suggests using Signal for people who want maximum security. Signal’s simpler design and transparency make it harder to exploit.
Apple’s head of security, Ivan Krstić, responded by stating that Apple found no evidence of targeted attacks and believes this was simply a software bug, not an active exploit.
What do you think about this iOS vulnerability? Do you think you might have been affected? Tell us below in the comments, or via our Twitter or Facebook.



























