News
Your Google Calendar might be the next target for hackers
The next time you get a Google Calendar notification, give it a second glance before you click.
Just a heads up, if you buy something through our links, we may get a small share of the sale. It’s one of the ways we keep the lights on here. Click here for more.
In an unexpected plot twist, hackers have set their sights on Google Calendar, turning our trusty scheduling tool into a playground for cyber mischief.
According to a report by TechRadar, hackers have discovered a method to use Google Calendar as a command and control (C2) infrastructure.
The digital villains of today face a challenge: getting malware on an infected endpoint to follow their nefarious commands. The traditional route involves compromised servers as C2 infrastructure.
But cybersecurity pros are quick on the draw, often discovering and terminating these connections in no time.
Enter the cunning hacker solution: use legitimate resources like Google Calendar, making it much harder for the good guys to detect the attack and cut the connection.
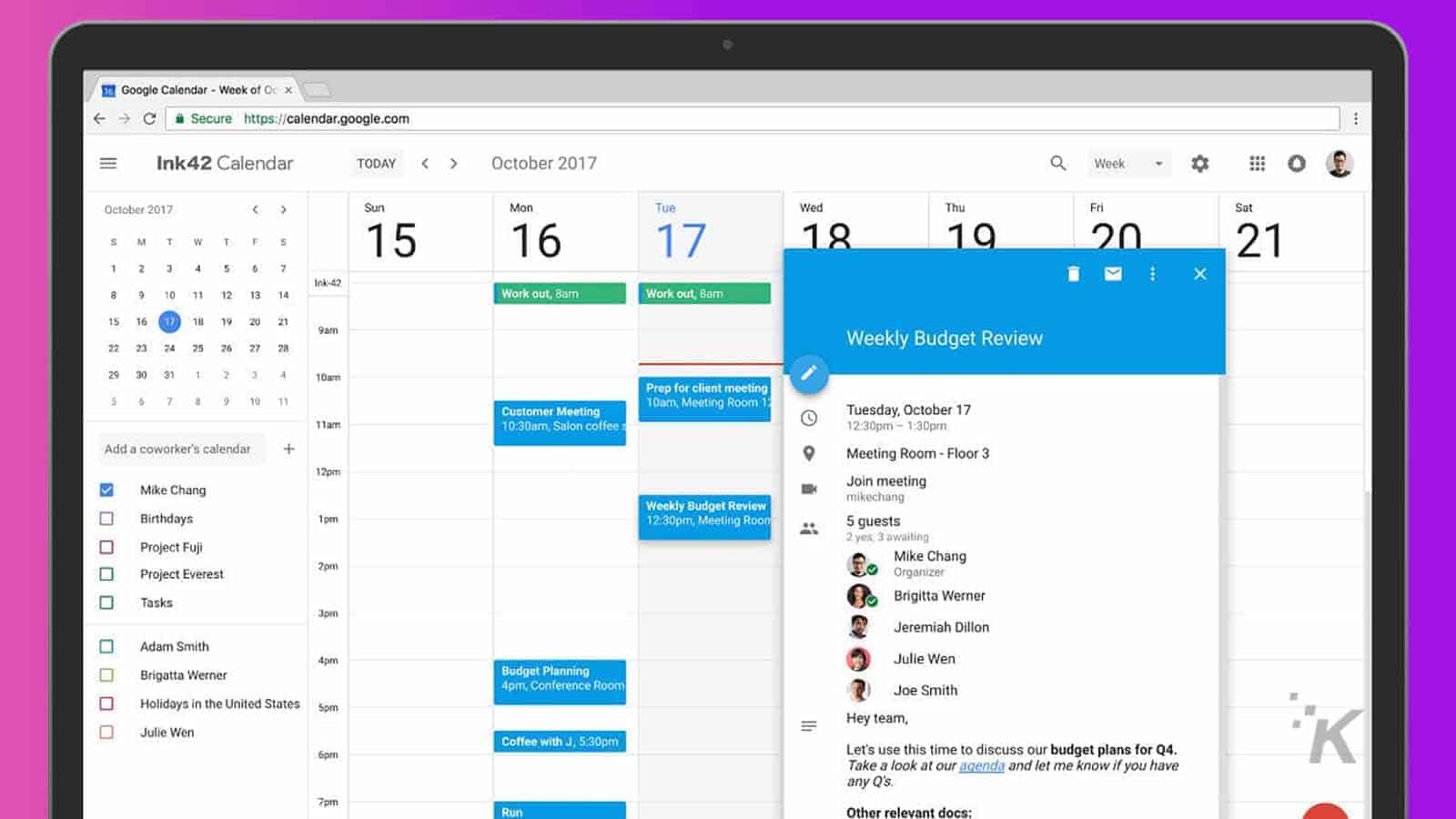
Google has issued a warning about a proof-of-concept (PoC) exploit known as “Google Calendar RAT” (GCR), which is currently making the rounds on the dark web.
This exploit, the brainchild of an individual known as MrSaighnal, creates a “covert channel” by exploiting the event descriptions in the calendar.

When a device is infected with GCR, it will periodically check the Calendar event description for new commands and execute them.
It then updates the event description with the command output. While there haven’t been any reported instances of GCR being exploited in the wild yet, it’s likely only a matter of time.
Hackers are increasingly turning to legitimate cloud services as vehicles for their malware
Google Docs, for example, has a share feature that allows users to type an email address in the document, prompting Google to notify the recipient that they have access to the file.
Some bad actors were observed creating files with malicious links and distributing them to email inboxes this way. Since the emails came from Google, they bypassed email protection services.
These developments serve as a stark reminder that even the tools we consider safe aren’t immune to exploitation. We need to stay vigilant and proactive in our cybersecurity practices.
So, next time you get a Google Calendar notification, give it a second glance before you click. After all, it’s better to be safe than sorry.
Have any thoughts on this? Drop us a line below in the comments, or carry the discussion to our Twitter or Facebook.
Editors’ Recommendations:
- Own this garage door opener? Shut it down; hackers can target it
- A major new Android bug lets hackers take over your devices
- Google Home speakers were at risk of eavesdropping hackers
- ‘Bahamut’ hackers target Android users with phony VPN apps