News
US government websites are hosting porn, malware, and sex toys
Officials say attackers abused user-upload tools, like a group calendar, to sneak in AI-generated porn.
Just a heads up, if you buy something through our links, we may get a small share of the sale. It’s one of the ways we keep the lights on here. Click here for more.
Local government websites are supposed to be boring: hours, permits, maybe a recycling schedule if you’re lucky.
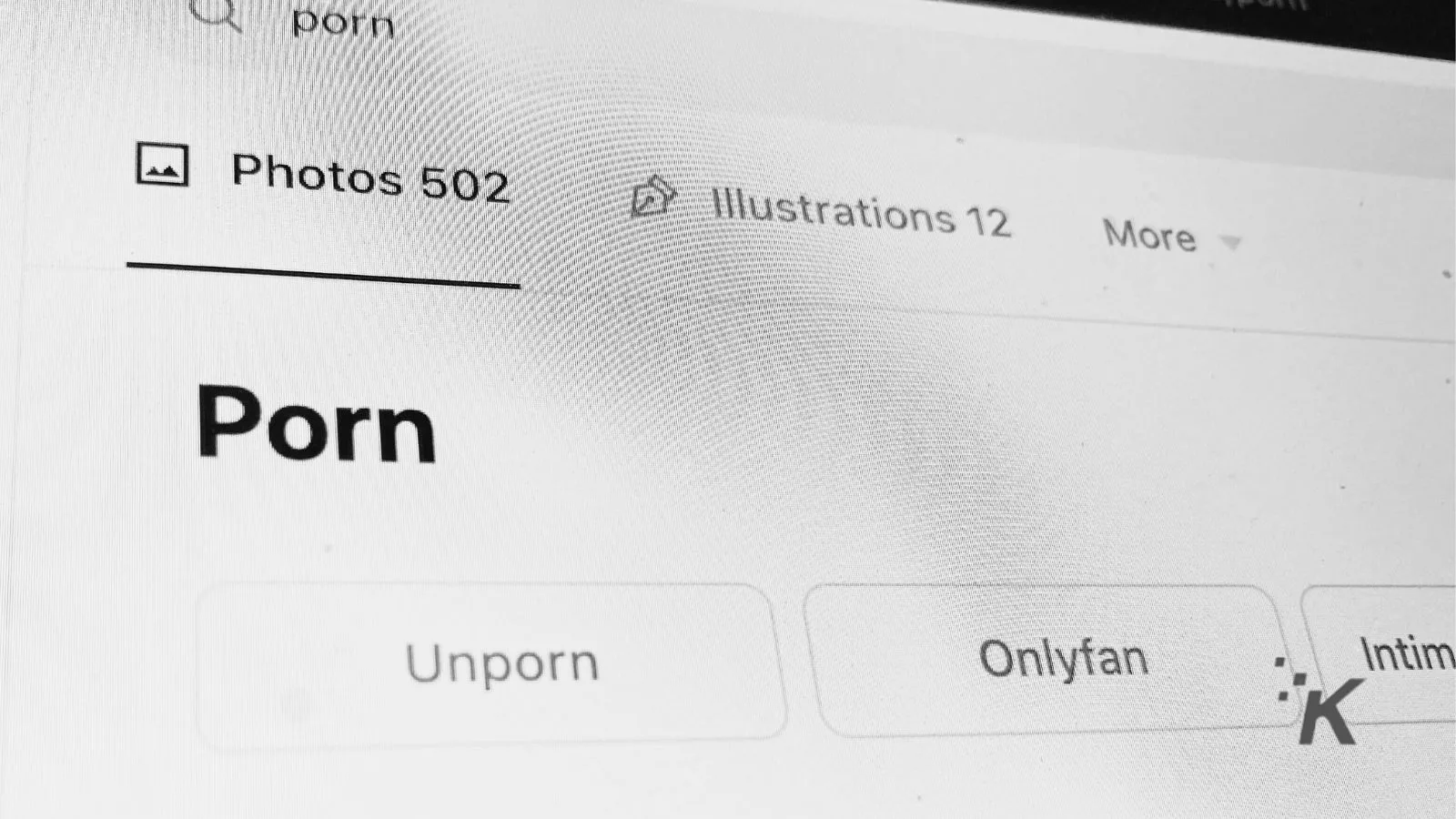
According to a new report from 404Media, though, a surprising number of them are now hosting something a little spicier: porn links, scammy redirects, and malware dressed up as innocent-looking PDFs.
The issue has popped up all over the map.
Municipal sites in places like Irvington, cultural institutions like the New York State Museum, and even federal websites such as Reginfo.gov, run by the General Services Administration, have all been caught hosting PDFs that quietly link out to porn sites, shady apps, and outright malicious downloads.
The problem was flagged by researcher Brian Kelly, who has been methodically notifying agencies and local news outlets in hopes of cleaning up the digital mess.
So how does a government website end up one click away from a sex toy retailer? It depends on the state.
In Washington, officials say attackers abused user-upload tools, like a group calendar, to sneak in AI-generated porn.
Agencies, including the Washington Department of Fish and Wildlife and the Washington Department of Veterans Affairs, traced the uploads to ten IP addresses and blocked them.
Elsewhere, the explanations get even more bleakly technical.
Indiana blamed a “significant surge in bot activity” after a PDF explaining how to make deepfakes appeared on the Indiana Department of Health website.
California said its document-upload portal was attacked.
And Nevada Department of Transportation pointed fingers at a third-party vendor, Granicus, which supplies web tools to thousands of government organizations.
The good news: once agencies know about the rogue PDFs, they’re easy to remove.
The bad news: malicious redirects keep lingering, occasionally whisking unlucky users off to malware, or, in one documented case, a page selling “realistic” animal-themed sex toys.
It’s admirable for governments to support public health. But maybe not like this.