Security
Mitigating threats with cyber threat intelligence feeds
Even though cybersecurity risks seem to become more sophisticated each year, several threats remain lucrative attack entry points.

Just a heads up, if you buy something through our links, we may get a small share of the sale. It’s one of the ways we keep the lights on here. Click here for more.
Enterprises get bombarded by cybersecurity threats day in and day out. Some business managers turn off their computers and call it a day only to find out the next day that their networks have been hacked. Threat actors don’t seem to rest and neither cybersecurity teams can afford to. Employing the cybersecurity insights brought by cyber threat intelligence feeds may be of help here.
Threat intelligence sources can help security teams monitor possible threats, giving them the time to investigate and react before these become real. These are five of the risks that cyber threat intelligence feeds can help security teams keep an eye on.
Typosquatting Campaigns
Possibly one of the oldest tricks in the book, but typosquatting still works. After all, the similarity between bankofamerica[.]com and bankofamerica[.]ooo is uncanny. Threat actors only need to imitate how the bank’s official website URL looks, and an unsuspecting payroll officer can type in the company’s online banking account details.
Threat intelligence sources, however, can help detect typosquatting domains as soon as they appear on the Domain Name System (DNS). By alerting security teams of a possible typosquatting domain, they prevent the domain from victimizing anyone in a connected network.
Phishing Attacks
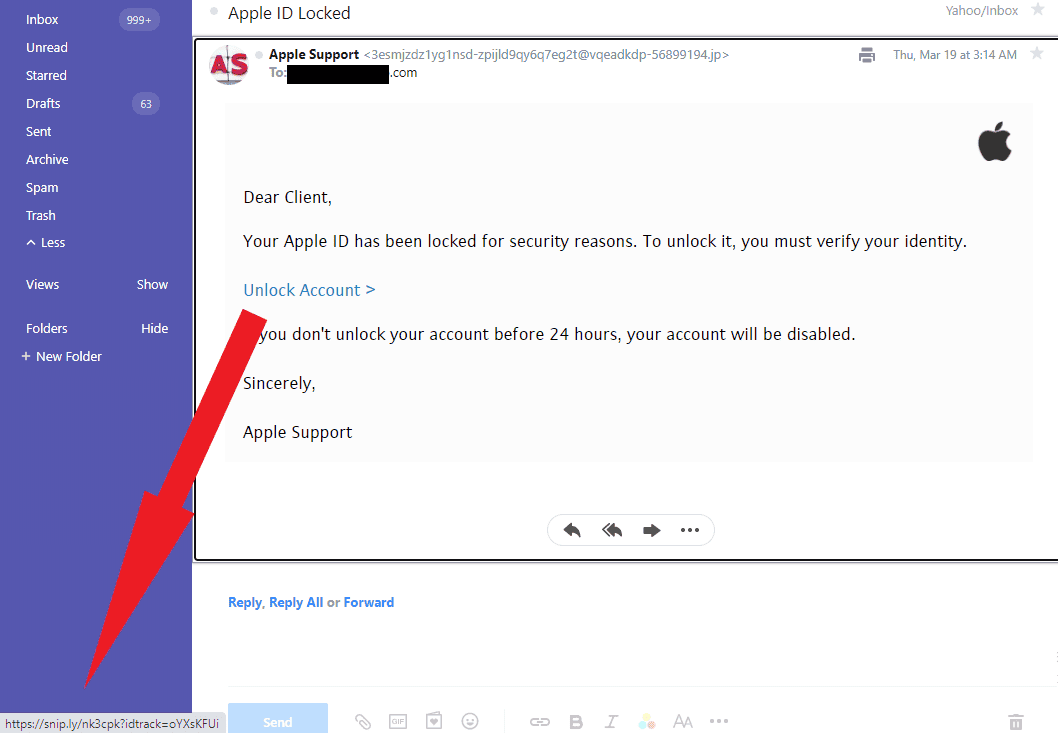
Like typosquatting, phishing is quite a common cyberattack entry point. In fact, typosquatting domains often figure in phishing campaigns, as emails coming from copycat domains look very authentic. Detecting typosquatting domains can, therefore, contribute toward detecting phishing attacks.
However, phishing campaigns can also use redirection techniques, such as an email address supposedly belonging to Apple Support.
The “Unlock Account” link redirects to snip[.]ly/nk3xpk?idtrack=oYXsFUi, a verified phishing URL. Cyber threat intelligence feeds can help pick up these URLs, preventing employees from accessing malicious sites and effectively protecting the company’s network.
DDoS Attacks
The distributed denial-of-service (DDoS) attack on GitHub in March 2018 was considered one of the largest at 1.3 terabytes per second (Tbps). That is, until June 2020, when an Amazon Web Services (AWS) client became the primary target of a 2.3Tbps attack. This means that threat actors are getting better in infecting devices and making them part of a botnet. Where do threat intelligence sources fit in this picture?
Security systems must be alerted of URLs that are possibly part of a botnet and connect to command-and-control (C&C) servers to mitigate DDoS attacks. Cyber threat intelligence feeds can provide such information. A good threat intelligence source can also identify the location of botnet controllers, and feed security systems with the decoded commands used for a specific attack.
Third-Party Risks
Some threat intelligence sources can check the reputation of a domain or an IP address and determine the risks associated with it. This feature is quite helpful when dealing with third parties, such as an outsourced payroll provider or when migrating to a third-party cloud computing service.
Third-party vendor risk assessment and monitoring should be a crucial part of an organization’s cybersecurity infrastructure. Allowing unverified third parties to access your network can leave your company’s data accessible to malicious actors. Look at what happened to Facebook in 2019. Two of its third-party app developers caused a significant data breach, which exposed more than 540 million Facebook user records.
Spam Campaigns
Spam email addresses often use disposable email domains. Threat intelligence sources can help block spam emails since some provide access to an exhaustive list of disposable domains.
Aside from sending spam, disposable domains can also be used by website abusers to take advantage of freemium features. We also see a fair share of them in phishing campaigns.
Even though cybersecurity risks seem to become more sophisticated each year, several threats remain lucrative attack entry points. Comprehensive threat intelligence sources that help mitigate a variety of cyber threats should thus be part of every organization’s cybersecurity efforts.
Editor’s Note: Jonathan Zhang is the founder and CEO of WhoisXML API—a domain and IP data intelligence provider that empowers all types of cybersecurity enterprises to build better products and achieve greater network security with the most comprehensive domain, IP, DNS, and cyber threat intelligence feeds. WhoisXML API also offers a variety of APIs, tools, and capabilities, including Threat Intelligence Platform (TIP) and Domain Research Suite (DRS).