Sponsored
How to prevent phishing: Your ultimate online safety guide
Follow this comprehensive guide to protect yourself against phishing threats and securely navigate the digital world.

Just a heads up, if you buy something through our links, we may get a small share of the sale. It’s one of the ways we keep the lights on here. Click here for more.
Key takeaways
- Phishing is a method cybercriminals use to trick people into revealing sensitive information. It can happen through emails, phone calls, text messages, fake websites, and social media.
- Email phishing involves fake emails from trusted sources to get you to click on malicious links or attachments.
- Spear phishing is personalized, using your personal info to seem legitimate.
- Vishing and smishing use phone calls and texts to extract personal data. Be cautious of urgent requests, check for spelling errors, and verify sender details to protect yourself from phishing attacks.
Phishing attacks exploit users’ trust in reputable companies by pretending to be legitimate organizations asking for sensitive information.
This comprehensive guide provides readers with best practices for recognizing, avoiding, and responding to phishing attempts in order to better protect their personal and financial data.
Understanding phishing: The basics
Follow the advice outlined in this guide to empower yourself against phishing threats and securely navigate the digital world.
Incogni – Personal Information Removal Service – Prevent Phishing
Understanding phishing attacks

What is phishing, and how does it work?
Phishing is a method used by cybercriminals to trick users into giving away sensitive personal information. They often send communications, such as emails, that convincingly pose as trustworthy sources.
These messages encourage recipients to click on links or provide login credentials, which then exposes their data to the scammers.
By taking advantage of people’s tendency to trust companies they know, phishers can stealthily access users’ financial accounts, passwords, and other sensitive information.
It’s an increasingly sophisticated threat that all digital users must understand to protect themselves.
Common tactics and schemes
While phishing originally manifested mainly through spoofed emails, attackers have expanded their methods to new channels:
- Email phishing: Fraudulent emails pretending to be from reputable sources to get users to click malicious links or attachments. Often used for delivering malware.
- Spear phishing: Highly customized phishing emails targeting specific individuals and organizations by incorporating personal details to appear more authentic.
- Vishing: Phishing attempts carried out over phone calls, often highlighting the urgency to pressure victims.
- Smishing: Phishing through text messages containing links to fake websites to harvest users’ financial and login information.
- Phishing websites: Fake websites impersonate real companies with the goal of stealing users’ login credentials and financial information.
- Social media phishing: Scams perpetrated through social media posts and messages directing victims to malicious links.
In all these forms, the goal remains to deceive users by impersonating trusted sources and entities to steal their personal data.
Understanding this range of tactics is the first step in protecting yourself.
Email spoofing and phishing emails

Email spoofing involves sending emails from a forged sender address, tricking recipients into believing that the message is from someone they trust, such as a well-known company.
These phishing emails often contain malicious links or attachments designed to steal personal information.
They may appear urgent, persuading you to act quickly without thinking, a common tactic to bypass your better judgment. The danger of these emails lies in their ability to mimic legitimate companies convincingly.
They exploit your trust, encouraging you to disclose sensitive information or download attachments that can compromise your computer’s security.
Recognizing these emails as fraudulent is crucial to protecting yourself from the potential financial and personal damage they can cause.
Spear phishing: A personalized threat
Spear phishing is a more insidious form of phishing where attackers use personal information about their target to craft a highly convincing and personalized message.
This could involve using details from your personal life gathered from social media or other sources to make the email seem legitimate.
The goal is to gain access to your sensitive information, such as payment details or login credentials, by exploiting your trust.
The personalized nature of spear phishing makes it significantly more dangerous than generic phishing attempts.
Attackers may reference recent transactions, personal interests, or even names of friends and family to lower your guard.
Recognizing these attempts requires a keen eye for detail and a healthy dose of skepticism, especially when an email asks for personal information or financial action.
Phishing attacks are constantly evolving, making it crucial to stay informed about the latest tactics used by scammers.
You can better protect your sensitive information from these cyber threats by understanding the various strategies employed, from email spoofing to spear phishing.
Vishing and smishing: Beyond the email

Vishing and smishing take phishing beyond emails, using phone calls and text messages as their mediums. In vishing, scammers call you, pretending to be from a trusted entity, and ask for personal information.
Smishing operates similarly, where scammers send text messages that may contain malicious links or request personal data. Both methods rely on the element of urgency, pressuring you into making quick decisions.
These tactics exploit the personal nature of phone calls and text messages, making the scam seem more legitimate. Sharing personal information through these channels can lead to identity theft and financial loss.
Recognizing these scams is vital for protecting yourself, emphasizing the need for caution when receiving unexpected requests for personal information via call or text.
The danger of websites and social media phishing
Phishing websites and social media phishing represent a significant threat in the digital world.
These websites mimic legitimate sites to steal your information, while social media platforms are used to spread malicious links or impersonate real users.
Both methods are designed to deceive you into handing over personal details or login credentials.
The interactive nature of social media makes it an ideal environment for phishing scams, where fake profiles can easily be created to interact with and deceive users.
Being vigilant about the links you click on social media and the authenticity of websites you visit is crucial for safeguarding your personal information against these sophisticated phishing attempts.
Recognizing phishing attempts
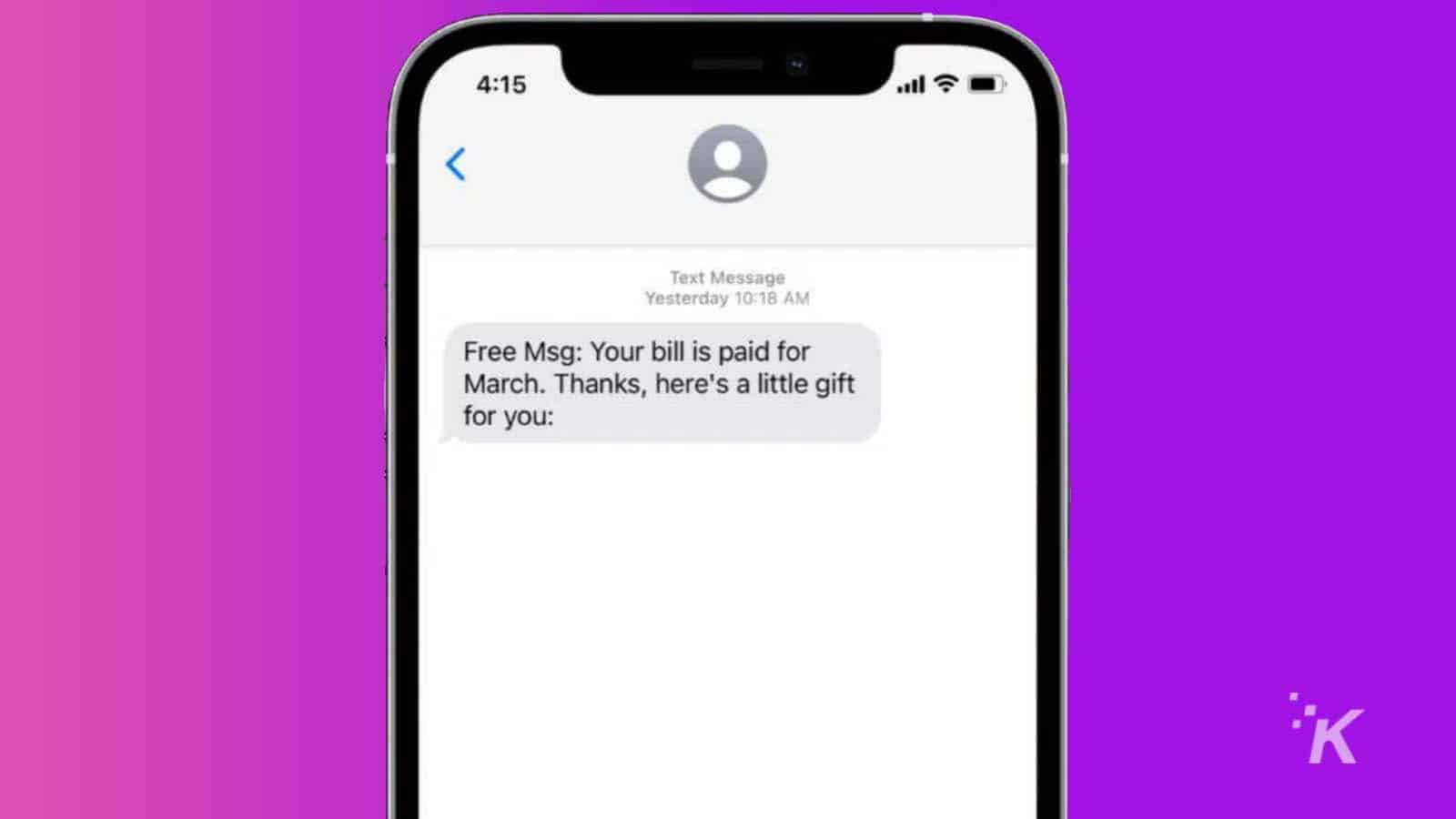
Warning signs of a phishing attack
Recognizing signs of a phishing attack can help you avoid falling victim to these scams.
Spelling and grammatical errors in emails or messages are common red flags, as legitimate companies typically review their communications carefully.
Other warning signs include requests for personal information or financial action, which reputable companies would not ask for via email or text.
Additionally, be wary of emails or messages that create a sense of urgency, pressuring you to act quickly. These are tactics designed to cloud your judgment.
Paying attention to the sender’s email address or the URL of a link can also help you spot phishing attempts, as they often contain slight discrepancies from legitimate addresses.
Deciphering phishing emails: What to look out for
Deciphering phishing emails involves looking for specific indicators that something is amiss. A generic greeting, instead of a personalized one, can be a telltale sign of a phishing attempt.
Similarly, receiving a fake invoice for a product or service you did not purchase should immediately raise suspicions.
These emails often contain links or attachments that can compromise your security when clicked or downloaded.
Being cautious and critically analyzing the content of suspicious emails is key.
Look for inconsistencies, verify the sender’s legitimacy, and never act impulsively by clicking on links or providing personal information without thorough verification.
This cautious approach can significantly reduce the risk of becoming a phishing victim.
Phishing prevention strategies

Strengthening your email security with spam filters
Strengthening your email security with spam filters effectively prevents phishing attempts from reaching your inbox.
Spam filters analyze incoming emails for suspicious content, blocking potential threats before you even see them.
Setting these filters to a high-security level can significantly reduce the risk of phishing emails slipping through. Besides spam filters, being proactive in your email management is crucial.
Regularly updating your email settings, being cautious with the information you share online, and educating yourself about the latest phishing tactics all contribute to a strong defense against these cyber threats.
Together, these strategies form a comprehensive approach to safeguarding your personal and financial information from phishing attempts.
The role of antivirus software in phishing prevention
Antivirus software plays a crucial role in preventing phishing attacks by scanning incoming emails and detecting suspicious links or attachments that could be harboring phishing threats.
When it spots a potential threat, the software alerts the user, preventing them from inadvertently downloading malware onto their device.
This proactive approach helps to safeguard sensitive information from cybercriminals looking to exploit vulnerabilities through deceptive emails and links.
Beyond just scanning and alerts, antivirus software often includes additional layers of protection.
These can range from real-time internet browsing safeguards to behavior-based detection that identifies and blocks unusual activity indicative of phishing or other malicious attempts.
By continuously updating to recognize new threats, antivirus software remains an essential tool in the fight against phishing, offering users peace of mind as they navigate the online world.
Direct website access vs. clicking links

The importance of regular software updates for security
Regular software updates are crucial for digital security, especially in preventing phishing. Developers release updates to fix vulnerabilities used by cybercriminals in phishing attacks.
Keeping software current strengthens protection layers, making it harder for attackers to breach defenses.
Security software, in particular, benefits from frequent updates, improving its ability to detect and counter new phishing techniques and threats. Ignoring update notifications can make users vulnerable to phishing scams.
These updates are essential security measures that address risks and enhance system resilience. Users can protect their devices and personal information by automating updates or setting reminders for evolving cyber threats.
Protecting your personal information

Safeguarding personal information is crucial to avoid falling victim to phishing attacks.
By adopting strong security measures like using complex passwords and staying vigilant against suspicious emails, individuals can effectively lower their risk of being deceived into disclosing sensitive data.
Managing your online presence and privacy settings
To prevent spear phishing attacks, individuals should limit the visibility of personal information on social media by adjusting privacy settings on platforms like Facebook, Twitter, LinkedIn, Instagram, and
Being vigilant and cautious while interacting online is essential to avoid falling for sophisticated phishing attempts that could compromise personal data.
Regularly reviewing and updating privacy settings helps protect personal information from being accessed by attackers, making it harder for them to create convincing phishing messages.
The perils of public Wi-Fi and how to navigate them
Public Wi-Fi networks offer convenience but also pose significant security risks, including heightened exposure to phishing messages.
When criminals gain access to the same network, they can intercept data and deploy phishing schemes.
Using public Wi-Fi without protective measures, such as a virtual private network (VPN), leaves personal information vulnerable to interception.
A VPN encrypts data, making it unreadable to outsiders, including potential phishers.
Being mindful of the risks associated with public Wi-Fi and adopting protective measures are essential steps in maintaining online security.
Instead of relying on unsecured networks, consider using a mobile hotspot for a more secure connection.
This significantly reduces the chances of falling victim to phishing messages and other cyber threats that exploit the vulnerabilities of public Wi-Fi.
Keeping your apps and devices secure

Regularly applying security patches to apps and devices is critical for maintaining online safety.
These patches address vulnerabilities that could be exploited by phishing scams and other forms of cyberattacks.
Ignoring update notifications can leave software exposed to newly discovered threats, making it easier for attackers to succeed in their malicious endeavors.
Developers continuously work to identify and fix security flaws, releasing patches as part of updates.
By ensuring that all software, from operating systems to applications, is kept up-to-date, users can protect themselves against the exploitation of known vulnerabilities.
This proactive approach is a key element of a comprehensive strategy to safeguard personal and sensitive information from phishing attacks and other security threats.
Avoiding data brokers and securing your contact information
Data breaches and security threats can expose personal information, making individuals targets for phishing attempts.
One way in which scammers obtain personal details is through data brokers, who compile and sell lists of contact information.
Being aware of how personal data is shared and taking steps to limit exposure is crucial in reducing the risk of phishing.
This includes being cautious about sharing personal information online and regularly checking settings on social media and other platforms.
Opting out of data broker lists and securing contact information are effective strategies for minimizing the risk of receiving unsolicited and potentially malicious texts or emails.
By controlling who has access to personal details, individuals can make it more challenging for scammers to target them with phishing schemes.
Regular vigilance and proactive measures are key in protecting against the misuse of personal information.
In the event of a phishing attack

Experiencing a phishing attack can be distressing, but taking prompt, informed action can mitigate the impact.
Understanding the immediate steps to take following a phishing attempt is crucial in protecting personal information and preventing further damage.
This includes changing passwords, monitoring accounts for suspicious activity, and reporting the incident to relevant authorities. Awareness and preparedness are vital in responding effectively to phishing attacks.
Immediate steps to take if you’ve been phished
If you fall victim to a phishing attack, the first course of action is to change passwords for all affected accounts. This helps secure accounts from further unauthorized access.
Using unique passwords for different accounts is also important to prevent a single breach from compromising multiple services.
Notifying banks or financial institutions about potential fraud can also help protect financial assets.
Becoming a victim of identity theft as a result of a phishing attack requires immediate reporting to law enforcement and relevant financial institutions.
Documenting the details of the phishing attempt can be invaluable during the investigation. Quick action can help recover losses and prevent further exploitation of personal information.
Reporting Phishing: What you need to know

Reporting a phishing attempt is a critical step in combating cybercrime. It not only helps in potentially catching the perpetrators but also aids in raising awareness about current phishing tactics.
Victims of phishing should report the incident to the Federal Trade Commission (FTC), their internet service provider, and any other relevant platforms that were mimicked or involved in the attack.
Individuals contribute to a broader effort to track and prevent phishing activities by sharing details of the phishing attempt with authorities.
Reporting can also trigger alerts to warn others of the scam, helping to prevent further victims. Cooperation and communication are key components in the fight against phishing and protecting the online community.
How to check for exposure of sensitive information
After a phishing attack, it’s crucial to assess the extent of any potential exposure of sensitive information.
Vigilance in monitoring bank statements, credit reports, and online accounts for unauthorized activity can help detect signs of misuse of personal data.
Tools and services that monitor personal information for signs of fraudulent activity can provide an additional layer of security.
Looking for unauthorized transactions or changes in account details can indicate that personal information has been compromised.
In addition, websites that display a padlock icon in the address bar indicate secure connections, reducing the risk of information being intercepted during transmission.
Regularly checking for these signs can help individuals identify and respond to security breaches more swiftly.
Spear phishing and high-target attacks

Understanding spear phishing
Spear phishing represents a highly targeted form of phishing where attackers gather personal information about their target to tailor their fraudulent attempts.
Unlike broad phishing campaigns that target masses, spear phishing focuses on specific individuals or companies, using detailed knowledge about their personal lives, jobs, or hobbies.
This meticulous approach makes spear phishing particularly dangerous and effective, as the emails or messages received seem incredibly credible, often mimicking communication from a trusted colleague or institution.
Spear phishing often aims to trick the recipient into divulging sensitive data, such as usernames, passwords, or financial information.
By leveraging details that seem only accessible to someone familiar, attackers increase their chances of success.
This could involve emails requesting urgent action, like updating payment details or transferring funds, making it paramount for individuals and organizations to recognize and guard against these personalized threats.
Protecting yourself from targeted attacks
Guarding against spear phishing requires a multifaceted approach. Firstly, implementing stringent spam filters helps to screen out many suspicious emails.
However, given the sophistication of these attacks, additional protection layers are necessary.
One of the most effective methods is multi-factor authentication (MFA), which adds an extra layer of security by requiring more than just a username and password to access accounts.
This means even if attackers obtain your credentials; they can’t easily breach your accounts without also having access to your phone or another form of identification.
Beyond technological solutions, staying informed and cautious plays a crucial role. Always verify the sender’s information before responding to requests for personal or financial information.
Be wary of unsolicited attachments and links, and adopt a policy of directly navigating to websites rather than clicking on links in emails.
This proactive stance, combined with strong security measures, significantly reduces the risk of falling victim to spear phishing and other targeted attacks.
Advanced phishing prevention techniques
Security awareness training: Your first line of defense
Preventing phishing attacks can’t rely solely on technical defenses; education is equally critical.
Security awareness training empowers employees to recognize and respond correctly to phishing attempts, including the more sophisticated spear phishing.
Through regular training sessions and simulated phishing campaigns, employees learn to spot phishing emails and understand the importance of reporting suspicious activities.
This enhances an organization’s overall security posture and fosters a culture of vigilance and continuous improvement.
Organizations can significantly mitigate the risk of data breaches by emphasizing the potential consequences of falling for phishing scams and reinforcing the correct reporting protocols.
Continuous monitoring and updating of training content ensure that employees are prepared to face evolving phishing tactics, making security awareness training an indispensable part of any comprehensive security strategy.
The benefits of using safe browsing tools
Phishing scams often involve directing victims to fraudulent websites that mimic legitimate ones. Safe browsing tools play a crucial role in identifying and blocking access to these deceptive sites.
By analyzing websites against a database of known phishing and malicious sites, these tools can prevent users from inadvertently disclosing their personal or financial information to scammers.
Alerts warn users before they navigate to a dangerous website, providing an effective preventive measure against phishing scams.
Always double-check the URL of a website before entering sensitive information to ensure it’s a legitimate site and not a clever imitation.
Employing safe browsing tools as part of a broader security strategy helps protect against the risks posed by phishing scams, safeguarding users’ data and privacy in an increasingly digital world.
The importance of multi-factor authentication

Multi-factor authentication (MFA) adds a critical layer of security that can thwart phishing attempts.
By requiring additional verification beyond just a username and password, MFA makes unauthorized access to accounts much more challenging for attackers.
Whether it’s a code sent to your phone, a fingerprint, or facial recognition, this second layer of security means that stealing your passwords alone isn’t enough for cybercriminals to gain access to your sensitive information.
Implementing MFA across all accounts, especially those containing personal or financial information, significantly reduces the risk of being compromised.
As a straightforward yet powerful security measure, MFA is essential in defending against phishing and a wide range of online threats.
Empowering yourself against phishing

Staying ahead of phishers: A continuous effort
The fight against phishing requires constant vigilance and a proactive approach.
Given phishing scams’ sophistication and evolving nature, individuals and organizations must stay informed about the latest threats and implement robust security practices.
This includes using complex, unique passwords for different accounts, employing password managers, and ensuring that personal and financial information is shared only over secure, trusted platforms.
Additionally, leveraging services like Incogni can help keep your data off the market by targeting and removing your information from data brokers’ lists.
These brokers often collect and sell personal data, which can end up in the hands of phishers.
Minimizing your digital footprint and enhancing your privacy reduces the risk of being targeted by phishing scams and other digital threats.
Cultivating a culture of security awareness

A well-informed and cautious user is the best defense against phishing attacks.
Organizations should strive to cultivate a culture of security awareness, where employees are encouraged to question unusual requests, especially those asking for personal or financial information.
Regular training, simulated phishing exercises, and clear communication on how to report suspected phishing attempts are key to building this culture.
In addition to organizational efforts, individuals should adopt good online hygiene practices, such as verifying sender addresses and phone numbers, being cautious with links in emails and direct messages, and using anti-phishing protection tools.
Together, these strategies form a comprehensive defense against phishing, protecting sensitive information and financial accounts from unauthorized access.
Protect yourself further with Incogni
 Incogni – Personal Information Removal Service – Prevent Phishing
Incogni – Personal Information Removal Service – Prevent Phishing
Incogni protects your phone number by preventing it from being sold to spammers. Incogni cuts off the source of the problem and saves you from the endless cycle of receiving unwanted calls.
- Hassle-free removal of personal information from various websites and platforms.
- Scans a wide range of websites and platforms to ensure thorough removal of personal information.
- Quick removal of sensitive data reduces the risk of identity theft and scams.
While being vigilant against phishing threats is critical, preventing your personal information from ending up on data broker lists provides another layer of defense.
Data brokers often collect and sell user data, which may be used for marketing purposes or fall into the hands of scammers, enabling more targeted phishing attacks.
Incogni is a service that identifies data brokers likely to have your personal information and sends automated requests to delete your data.
By reducing your digital footprint, Incogni limits data availability to put you at lower risk of phishing schemes.
Key features
- Identifies and tracks data brokers holding personal information
- Sends regular opt-out requests for data deletion
- Offers customizable dashboard to monitor removal progress
- Provides discounted subscription for guide readers
Subscribers can keep their data off the market with a 1-year Incogni subscription for just $6.49/month (50% off the regular price). Take control of your digital privacy while also enhancing protections against phishing and other attacks.
Have any thoughts on this? Drop us a line below in the comments, or carry the discussion to our Twitter or Facebook.
Editors’ Recommendations:
Disclosure: This is a sponsored post. However, our opinions, reviews, and other editorial content are not influenced by the sponsorship and remain objective.