Security
How to protect your IoT devices from going rogue
Let’s face it, eventually someone will hack your IoT device. Here’s how to prevent it.

Just a heads up, if you buy something through our links, we may get a small share of the sale. It’s one of the ways we keep the lights on here. Click here for more.
Let’s face it, eventually someone will hack your IoT device. Here’s how to prevent it.
The Internet of Things (IoT) dubbed by many catchy monikers such as Internet of Trash, or Internet of Terror to account for the vulnerabilities present in the Internet-connected devices is increasingly making a home in our daily life.
What is Internet of Things? IoT is a concept of connecting mobile devices to a single Internet-connected the cohesive network. In simple terms, every device can connect to the internet. Things like smart refrigerators, internet cameras, smart thermostats, even washing machines fall into the category of IoT. These devices while presenting the opportunity to automate your everyday life, also offers a platform opportunity to cybercriminals for new attacks.
Now, these attackers leverage the new IP-based connected devices to launch historical Distributed Denial of Service (DDoS) attacks. A few weeks ago news reports made headlines after a massive DDoS attack by Mirai malware shuts down famous sites including Twitter, CNN, Netflix, GitHub, Amazon, SoundCloud, and many others by affecting renown hosting provider DynDNS.
So, what are the inherent risks associated with IoT-connected devices? And what are the best practices to protect home devices from such attacks?
We will be looking at these aspects and discuss the best ways to ensure your devices are not affected by malware.
IoT Security Issues
When we mention IoT to security experts, the security babble becomes an unbearable ordeal. There is no unification in theories, protection, or coding methods for these devices. People have their ideas and opinions on how to best protect the IoT devices.
Some argue to apply a firewall like a device to regulate the control of the device. Some support the use of a certificate-based option only to allow parties with authorized security certificates to monitor the device thus removing the unauthorized entities from the equation. In the debacle, there are so many options that the easiest ones are missed.
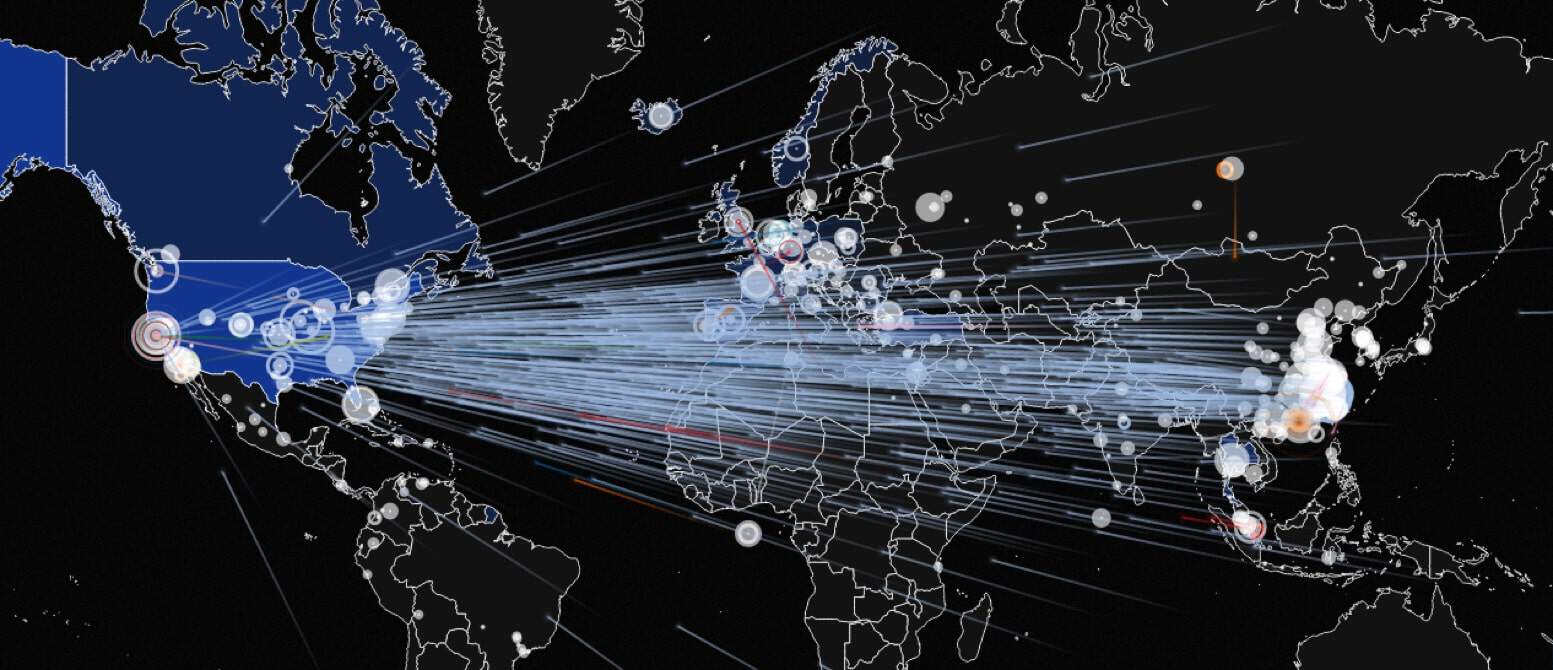
A few weeks ago, the Mirai source code was leaked on the internet. The first massive attack was experienced when botnets (compromised IoT devices) infected by Mirai malware attacked Brian Krebs website. The 620 Gbps traffic generated by the compromised devices was so immense for the company Akamai that they had to remove Brian Krebs site from its servers. Fortunately, Google stepped in utilizing their Project Shield, a service aimed to assist public-facing people and journalists that incur a DDoS attack.
A major distributed-denial-of-service (DDoS) attack on cybersecurity blog Krebs on Security reminded technology users that faulty Internet of Things (IOT) security makes all of our devices and appliance vulnerable. But some manufacturers may not be willing to spend money to make their appliances more secure,” said Electronic Frontier Foundation (EFF) Senior Staff Attorney Lee Tien, “it would be a lot easier and a lot cheaper to design it without having storage and all sorts of things that people think they should have.
While everyone was talking about this incident, another record-breaking attack of 1 Tbps generated traffic struck France-based web hosting company OVH, but the company was able to pull off from the attack.
The malware is basic, and experts consider it not completed after analyzing the code. The issue remains that the malware still works well and causes such havoc. It has three components; a command and control center for communication, a network scanner to search weak devices, and an attack module.
The malware infected IoT devices by scanning a network and abusing Telnet protocol that was created in 1969 and offers the most vulnerable security, which should be made redundant now in 2016. The scary part is that the compromised devices contain one of 65 known passwords used by the protocol Telnet to authenticate the device, which if utilized leads to compromise the device and turn it into a botnet.
IoT Protection

When using IoT devices, look at them as your computer. By following few of the practices, you can reduce the attacks or future infections that compromise your IoT devices.
Change the default password. It is somewhat considered as a chore. However, it is the easiest step to remove a vulnerability from your internet network.
Use HTTPs interface where possible. If you log in to a computer to manage your devices, with HTTPs gateway, it removes clear text or man-in-middle attacks from compromising your passwords or device security.
Turn it off like lights. If your IoT device offers extra communication protocols (Telnet, SSH, other) that are idle and have the ability to be turned off, then disable them. Removing the ports from listening mode will remove the potential ability for it to be exploited.
Utilizing these three basic and simple practices can significantly reduce the ability for a cyber-attack to use your IoT device as a traffic generating cyber weapon.