Google will delete data collected from Chrome’s Incognito Mode
Not out of goodwill, but as part of a proposed class-action settlement.

Just a heads up, if you buy something through our links, we may get a small share of the sale. It’s one of the ways we keep the lights on here. Click here for more.
Google has agreed to purge billions of data points collected from users of its Chrome browser while they were surfing the web in “Incognito” mode.
The agreement is part of a settlement stemming from a lawsuit brought by some consumers who claim Google was deceptive in their marketing and privacy disclosures related to Incognito mode.
While Incognito mode didn’t store certain information on a person’s computer, the browser continued to send certain data points to Google’s servers. Like other companies, Google uses these data points to track certain online behaviors, which helps it determine how people use Chrome.
The lawsuit claimed Google wasn’t fully transparent in how Chrome works, and that they were duped into believing their online activity wasn’t being tracked at all when they switched into Incognito mode.
Through the duration of the lawsuit, Google said it thoroughly informed users about what Incognito mode did and did not do. Still, the company wanted to avoid the expense that a lengthy lawsuit might bring, and ultimately agreed last year to settle the case out of court.

The terms of the settlement were not immediately available when KnowTechie covered the outcome last December, but now we know that the settlement includes no direct payment to any of the class action plaintiffs involved.
Instead, Google says it will delete billions of data points collected from millions of Chrome users that the company amassed before 2020 — the year the lawsuit was brought.
That condition and others in the settlement are still subject to the approval of a federal judge overseeing the case, though judges rarely reject settlements reached in civil litigation.
Even if the settlement is approved, individual plaintiffs who can point to specific losses will still be able to sue Google separately. At least 50 such cases have already been filed in California, according to the Wall Street Journal, which first detailed the proposed class action settlement on Monday.
Those cases could result in financial awards, in which Google is forced to pay plaintiffs if they can point to specific losses and prevail on those claims.
What Google Chrome’s Incognito Mode does — and doesn’t do
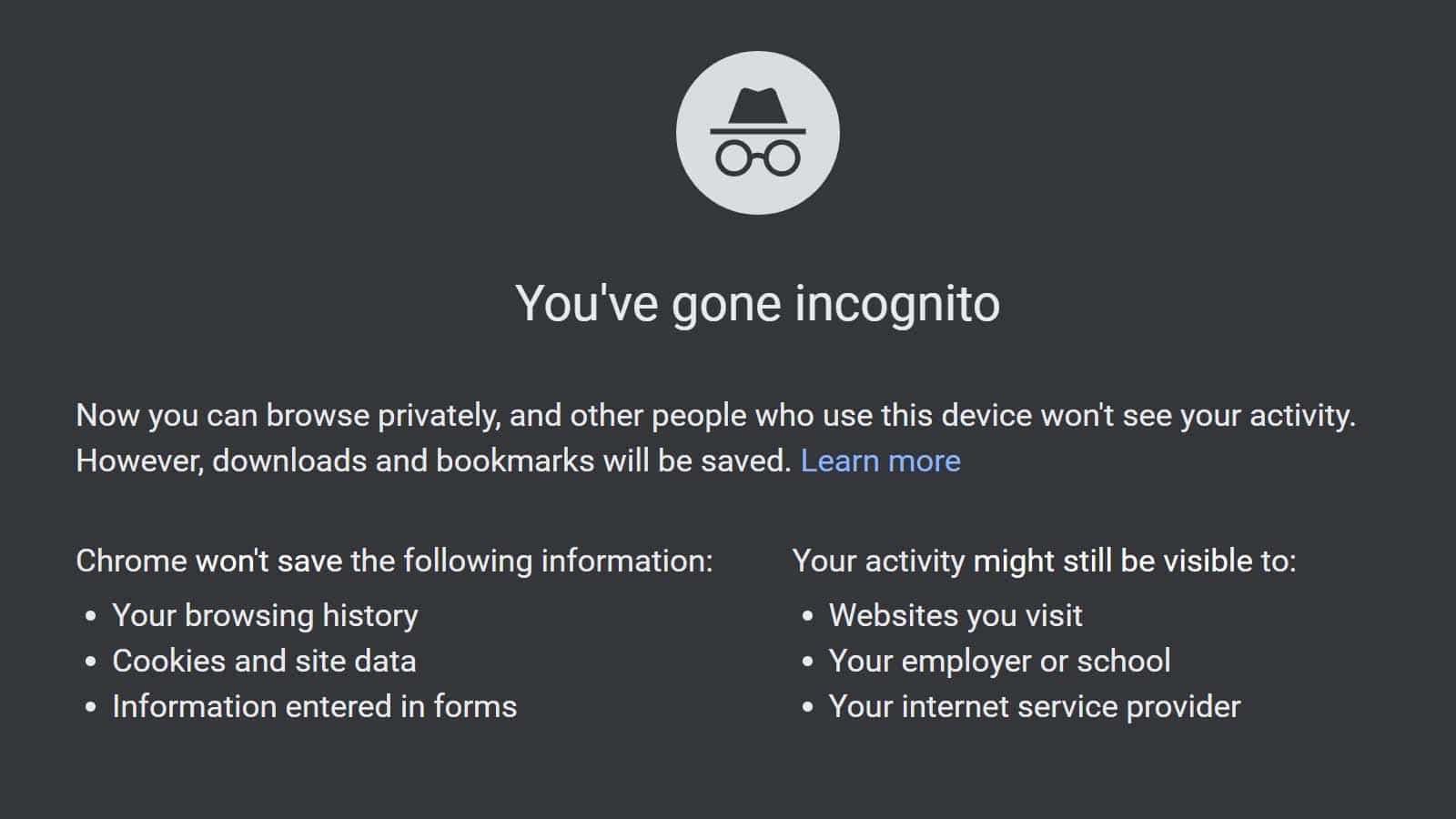
Back in 2022, KnowTechie first detailed the specific things Google Chrome does when a user switches the browser into Incognito Mode, with most of the information culled from a notification that appears via Google Chrome itself.
That notification has not changed much over time: Google still affirms that the Chrome browser won’t save a user’s browsing history, cookies, site data or information entered in forms while they’re surfing the web in Incognito Mode.
But some activity, like visited websites, might still be visible to companies and schools that manage the network that a computer is connected to — and that includes a home or wireless Internet Service Provider like Comcast, Charter, AT&T or T-Mobile.
In other words, Incognito Mode is intended to keep someone’s browsing history safe from the prying eyes of other people who might use a particular phone or computer — but it won’t keep the information from being collected or evaluated from anyone who operates a computer network.
That operator, apparently, includes Google, which receives certain data from websites that embed certain Google products like YouTube features or that incorporate Google platforms like AdSense into their web pages or services.
In some ways, this is a good thing: People browsing the Internet in Incognito Mode might want to stream a YouTube video, and Google needs to know which video that person wants to see.
That can only happen if the Chrome browser sends information from the computer to the Google server, where a YouTube video appears.
The same goes for certain advertisement tools, which help cover the costs of free-to-access websites (like this one!). Ideally, advertisements are only effective if they relate to something a person might be interested in.

Certain things, like the type of device a person is using or their rough geographic location based on their Internet connection, can offer some generalized insight into a website visitor.
iPhone users, for instance, are believed to earn a higher income than those who use Android, while someone living in a densely-populated city might have access to more goods and services than someone living in a rural area.
Knowing that, websites can tailor their advertising to a person without knowing specific, personal details about them — and that can be a good thing, especially for privacy-conscious people.
But Google not being fully transparent about how Incognito Mode works can be problematic. For years, Incognito Mode was designed to make it look like a person’s web activity was completely shielded from everyone — other people using a computer, service providers, website operators, even Google itself.
Through this lawsuit, we now have some affirmation from Google that isn’t accurate.
In 2021, a judge turned down an attempt by Google to have the class action lawsuit thrown out of court after finding that Google “did not notify users that [it] engages in the alleged data collection while the user is in a private browsing mode.”
By not making things clear, Google didn’t just put itself in a position of being sued — it also damaged its reputation with privacy-conscious consumers who believe Google made a deliberate decision to market Incognito Mode as offering certain privacy protections that weren’t actually available.
So, how do you stay completely private online?

The reality is, there isn’t much a person can do to remain completely private online.
It was once believed that taking certain steps like using encrypted messaging apps, virtual private networks (VPNs) and anonymized software like The Onion Router (Tor) browser were foolproof ways to keep people and their online activities totally private.
Through various civil and criminal cases, we now have enough evidence to show these methods aren’t entirely protective:
While most VPNs affirm they do not log the specific online activity of their users, some do keep logs of when an account is connected to one of their servers.
Those logs can be subpoenaed by law enforcement agencies, who are very good at connecting the dots back to a specific computer and, ultimately, a person.
VPNs are also vulnerable to the same cybersecurity incidents that afflict other companies, and hackers can be in a system for weeks collecting vast troves of (hopefully encrypted) user data without detection.
Encrypted messaging apps are also not a foolproof way to hide a person’s online activity.
Documents obtained by some publications through open records requests show how federal law enforcement agents can request certain user data from encrypted messaging apps like Telegram (might include IP addresses), Signal (dates and times of a user’s connection), and Wickr (date of last use).
As with VPNs, police are pretty good about connecting what little information they can get from encrypted messaging app providers, then connecting the dots back to a device and a suspect.

Even the Tor Browser, which was thought to be one of the best ways to hide online activity, isn’t as anonymous as once believed.
Last year, Motherboard revealed the FBI managed to locate the real-world IP address of a person who allegedly visited a terrorism-linked website, even though that person supposedly did so via the Tor Browser.
As of 2023, the FBI and the U.S. Department of Justice have refused to reveal how they managed to do what was thought to be impossible.
But they are hardly alone: There are numerous news reports of law enforcement officials in the United Kingdom and other countries doing the same thing (although some question whether this is simply a police scare tactic meant to deceive the public into believing the Tor Browser isn’t anonymous).
Police arresting people who commit crimes is, of course, a good thing. That is their entire job.
But law enforcement documents and legal cases point to one inescapable conclusion: There is no way to remain 100 percent anonymous on the web — not if you use a VPN, not if you use the Tor Browser, and definitely not if you use Google Chrome’s Incognito Mode.
That doesn’t mean a person shouldn’t practice good security measures to keep their online activity as private as possible.
In fact, VPNs like NordVPN or ExpressVPN are great tools for those who need to access public Wi-Fi connections on a regular basis, since they can make it difficult for unskilled hackers to access certain private information.
And Tor Browser has many practical uses for academics, researchers, journalists and activists who operate in countries where some or all of the Internet might be blocked by government agencies.
And reporters routinely use encrypted messaging apps to communicate securely with sensitive sources who pass on critical information and materials that are used in groundbreaking investigative journalism.
So, take certain protections and practice good Internet security principles — just don’t be fooled into thinking what you do on the Internet can’t be learned by someone else.
Have any thoughts on this? Drop us a line below in the comments, or carry the discussion to our Twitter or Facebook.
Editors’ Recommendations:
- AT&T discovers five-year-old data breach affecting millions
- New Florida law bans some teens from having social media accounts
- Amazon’s ‘Just Walk Out’ tech was just one big fat stupid lie
- Google engineers hack PlayStation Portal to run emulated PSP games




























