Android
Android users: Delete this app – it’s injected with a data-stealing Trojan
The app was downloaded over 10,000 times.

Just a heads up, if you buy something through our links, we may get a small share of the sale. It’s one of the ways we keep the lights on here. Click here for more.
Over 10,000 Google Play users have downloaded another malicious Android app stuffed with malware. Called QR Code & Barcode Scanner, the app also installed a remote access trojan (RAT), that let the attackers skim passwords, banking details, and other sensitive data.
Noticed by security researchers at Cleafy, the malicious app contains the TeaBot trojan. This nasty piece of software uses Android’s accessibility services to read the screen, then uses streaming software to send data to its controllers.
When it first came out, it was limited to watching a hard-coded list of around 60 banking apps. Now the attackers have expanded in scope, with over 400 applications on the watchlist. Those range from banking apps to crypto exchanges/wallets, and even digital insurance apps.
READ MORE: Android users: delete these apps – they could be stealing your money
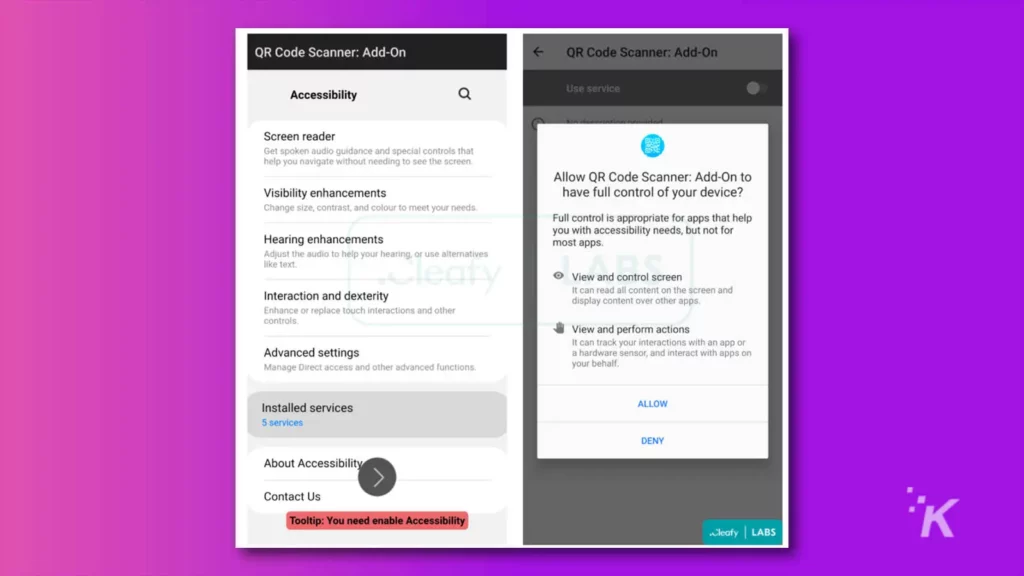
TeaBot was distributed inside a Google Play Store app called QR Code & Barcode Scanner. Google has pulled it from the Play Store at the time of writing, but over 10,000 people downloaded and installed it before that. If you have it on your device, delete it, and change all of your financial service passwords.
READ MORE: Android users: Delete these apps – they’re harvesting your data
The malware managed to get onto the Play Store by not actually being inside the app, to begin with. Once installed, and opened, it would ask the user to install an update.
This wasn’t actually a Google Play Store update, but a download of code from two GitHub repositories. That code installed TeaBot, which then asked the user to give it more permissions.
It’s clear that Android malware makers have figured out how to sidestep any protections the Google Play Store has. There are a few things that users can do to keep safe, however.
Only install updates from inside the Google Play Store, and not inside the app. Be wary of any app asking for extended permissions at install time. Be extra wary of any app that asks for extended permissions at any time after installation.
Have any thoughts on this? Let us know down below in the comments or carry the discussion over to our Twitter or Facebook.
Editors’ Recommendations:
- Android 13: News, features, rumors, leaks, release date, and everything we know so far
- Android 13 will finally let people adjust their flashlight brightness
- When is iOS 15.4 coming out?
- Apple App Store subscriptions raked in twice as much money as the Google Play Store in 2021