Just a heads up, if you buy something through our links, we may get a small share of the sale. It’s one of the ways we keep the lights on here. Click here for more.
Hey Chrome users, guess what? The party never stops. Just when we thought we had dodged a bullet with Google patching a zero-day vulnerability just a few days ago, another one pops up.
Google’s security team recently found themselves in a déjà vu situation, discovering a second zero-day exploit (CVE-2023-2136) just days after patching another one.
The good news is that they’re on it. “Google is aware that an exploit for CVE-2023-2136 exists in the wild,” Google wrote in a release update. Thankfully, a patch is being rolled out now.
| CVE ID | CVE-2023-2136 |
|---|---|
| Reference | National Vulnerability Database (NVD) |
| CVSS Severity Rating | High |
| Fix Information | Various fixes from internal audits, fuzzing and other initiatives |
| Vulnerable Software Versions | Prior to 112.0.5615.137 of Google Chrome |
| Description | Integer overflow in Skia in Google Chrome allowed a remote attacker who had compromised the renderer process to potentially perform a sandbox escape via a crafted HTML page. |
| References | MISC:https://chromereleases.googleblog.com/2023/04/stable-channel-update-for-desktop_18.html URL:https://chromereleases.googleblog.com/2023/04/stable-channel-update-for-desktop_18.html MISC:https://crbug.com/1432603 URL:https://crbug.com/1432603 |
| Assigning CNA | Chrome |
| Date Record Created | 20230417 (Disclaimer: The record creation date may reflect when the CVE ID was allocated or reserved, and does not necessarily indicate when this vulnerability was discovered, shared with the affected vendor, publicly disclosed, or updated in CVE.) |
What is it this time, Google?
The official report says that this flaw could allow a remote attacker, who’s already compromised the renderer process, to perform a sandbox escape through a crafted HTML page.
In plain English, it means they could run untrusted, malicious code on your computer and potentially spread infection. Yea, not good!
Now, you might be wondering if this is connected to the other zero-day vulnerability Google patched last Friday (CVE-2023-2033). We don’t know for sure, but both flaws seem to exploit specially crafted HTML pages so they could be related.
The good news is that Google’s been working double-time to patch these flaws. The fix for CVE-2023-2136 is already rolling out, arriving as Chrome version 112.0.5615.137.
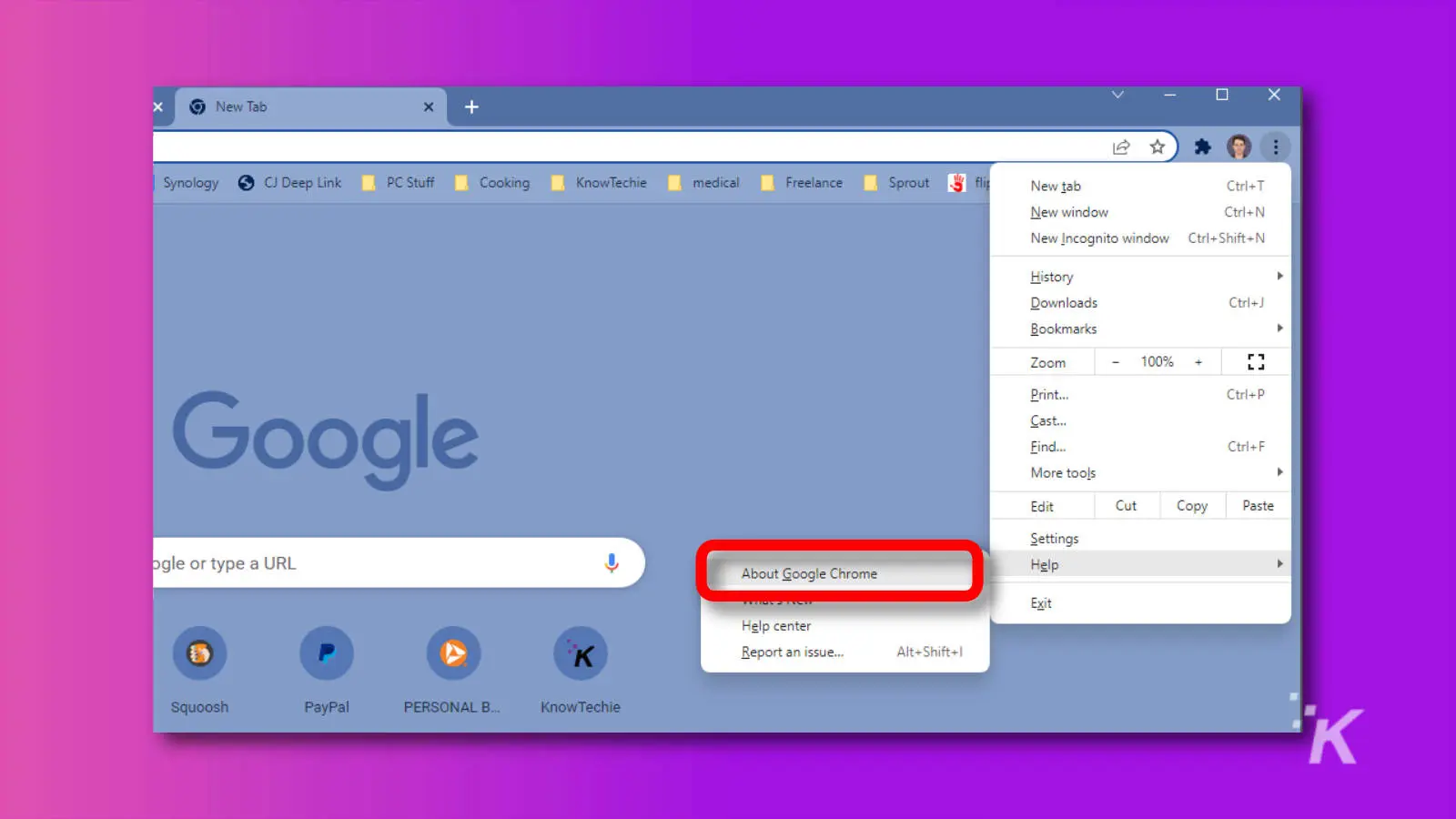
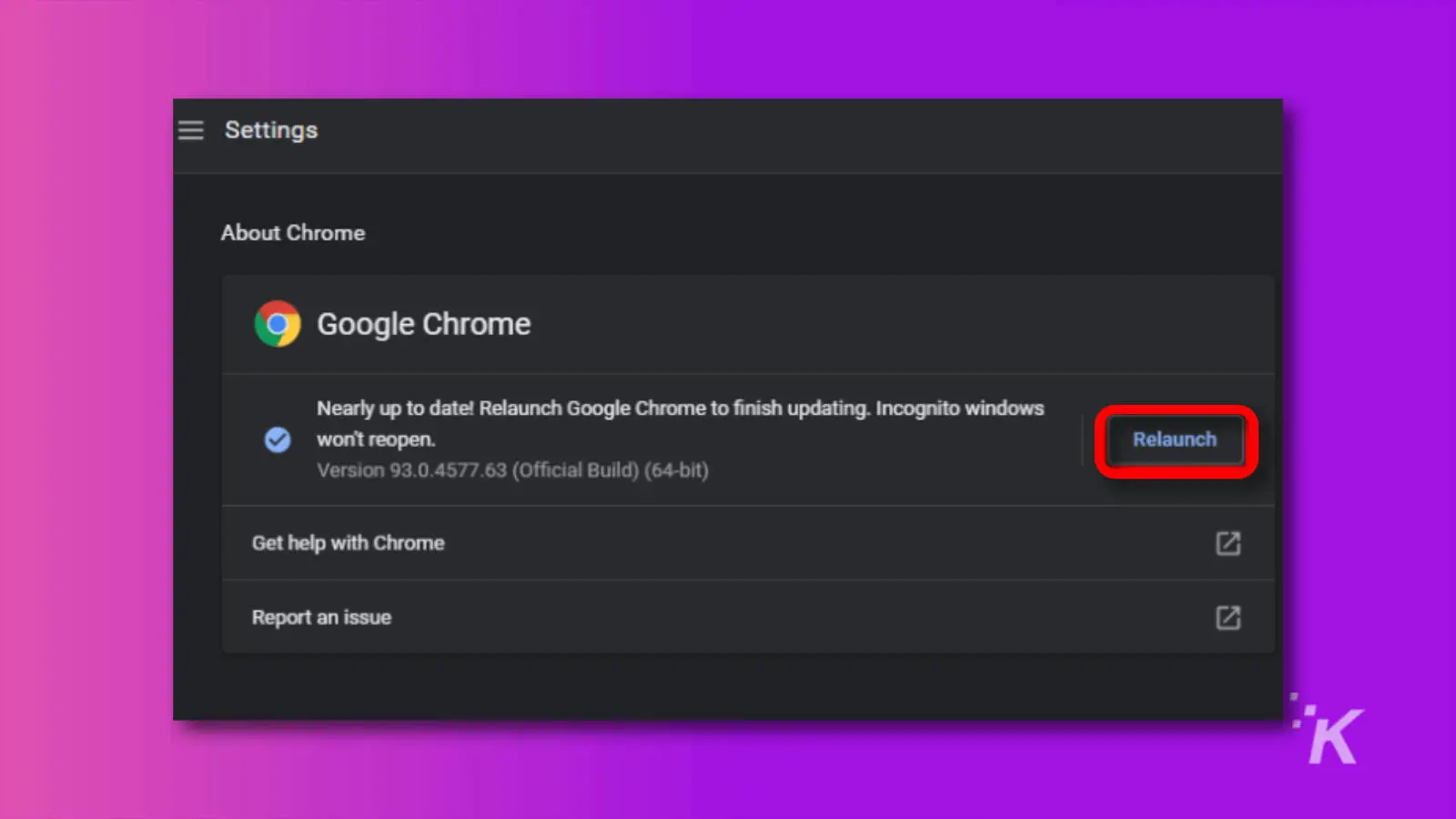
How to update Google Chrome
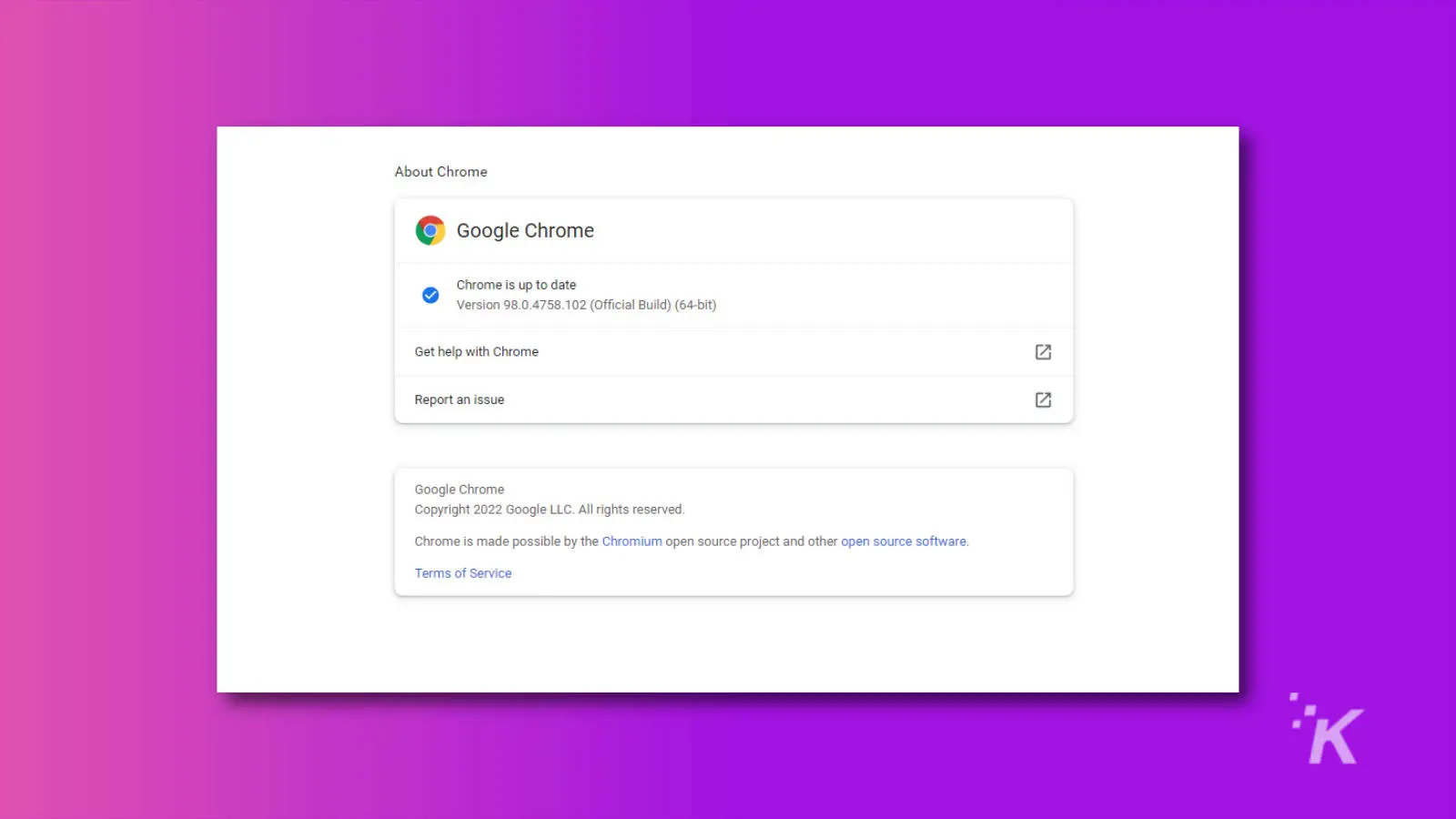
So, how do you update? Keep an eye out for that update button in the upper-right corner of your browser, or head to the “About Chrome” tab to automatically receive the update.
If you don’t feel like waiting, you can always manually update using the instructions below:
In the meantime, here are some tips to stay secure while browsing online:
- Keep your software up-to-date (like, right now with Chrome).
- Don’t click on suspicious links or open unknown attachments.
- Use strong, unique passwords for each account.
- Enable two-factor authentication whenever possible.
Remember, folks, the internet can be a wild place, but with a little vigilance and timely updates, we can keep our browsing experience as secure as possible. Stay safe out there.
Have any thoughts on this? Drop us a line below in the comments, or carry the discussion over to our Twitter or Facebook.
Editors’ Recommendations:
- Google is developing a new AI-driven search engine
- Google TV’s latest update adds 800 free live channels
- Did Google accidentally send you free money? Well, it’s yours to keep
- Google CEO pretty much confirms Chatbot integration with search