Internet
How to lessen the impact of cybercrime with domain research and monitoring solutions
Implementing cyber protection technologies, such as domain research and monitoring solutions, can minimize your exposure to threats.

Just a heads up, if you buy something through our links, we may get a small share of the sale. It’s one of the ways we keep the lights on here. Click here for more.
Cybercrime is big business. No longer the work of a few enterprising hackers, today’s new wave of cyberattacks is carried out by criminal networks with their own supply chain, no less. Also, data breaches have increased by 67% in the past five years, paving the way for a new underground economy that is worth billions of dollars.
Despite how sophisticated cybercrime has become, organizations can still curtail its impact with adequate cyber risk protection. Companies can prioritize domain intelligence, for instance, since public interfaces, such as emails and websites, are common attack vectors. Investing in domain research and monitoring tools can help them gauge their attack surface and significantly reduce risks brought on by threats. Let’s take a closer look at how this is possible through some components of the Domain Research Suite.
How Domain Research and Monitoring Solutions Help Curb Cyberattacks
Cybercrime persists because attacks are relatively easy to accomplish. Besides, there’s a thriving market behind it. Perpetrators can easily rent exploit kits or purchase ransomware or malware in the Dark Web to achieve their goals. Advanced persistent threats (APTs) are backed by deep-pocketed adversaries and even nation-states, allowing threat actors to go undetected as they exfiltrate confidential data from organizations.
However, the thing about the worst attacks is that they still leave traces behind. Besides, offenders are known to share resources, along with tools, tactics, and procedures (TTPs). Stricter access control and the right technologies can also help detect malicious activities. Domain research and monitoring tools can primarily assist with the following:
-
Creating Threat Profiles
Model-driven security goes beyond cataloging critical assets and their vulnerabilities. It involves examining possible attack scenarios specific to an organization. It also entails profiling potential internal and external threat actors to understand their motives and behavioral patterns.
Reverse WHOIS Search enables security analysts to retrieve the domains used by cybercriminals to further their goals. In fact, you can subscribe to government intelligence sources and industry threat reports to obtain a list of criminals’ names then use them as search terms to retrieve all connected domains.
As an example, we used “Danial Jeloudar” as a search term. Jeloudar is on the Federal Bureau of Investigation (FBI)’s most-wanted list for identity theft and payment card fraud. He used malware to steal information from vulnerable e-commerce sites and extort money from victims.
We used the tool’s Advanced search setting to scan for historical WHOIS records that contain his name:
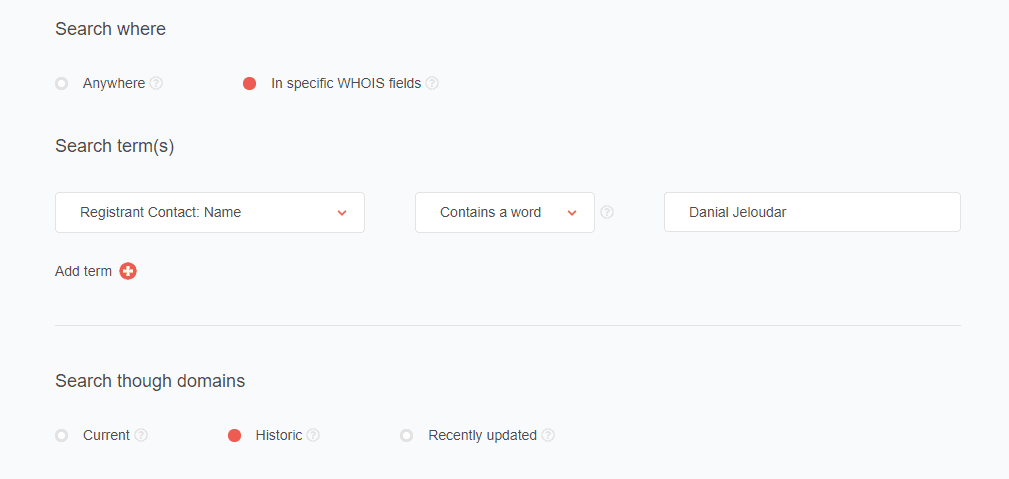
And we found eight connected domains:
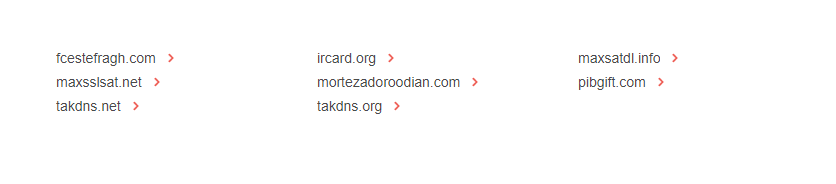
Analysts can subsequently inspect the WHOIS record of each domain in the list using WHOIS Search or WHOIS History Search to study the history of the domains’ ownership. That would reveal the domains’ name servers for further investigation. They can also use the WHOIS data to spot emerging patterns for their threat profiles. An example would be Jeloudar’s go-to top-level domain (TLD) extension or registrar.
-
Network Analysis and Protection
It’s best to block shady web addresses proactively to prevent your network from interacting with them. You can also keep an eye out on future activities of cybercriminals like Jeloudar via Registrant Monitor. This tool allows users to receive updates on domains registered or dropped by the registrants of interest.
Additionally, users can rely on WHOIS Search and WHOIS History Search to validate the legitimacy of the domains their users come in contact with. These tools can help them check the identities of suspected users. If the domains point to a proven phishing site, for instance, an attacker can be determined and prevented from causing more damage even if he/she uses different domains.
Implementing cyber protection technologies, such as domain research and monitoring solutions, can minimize your exposure to threats. With accurate and reliable domain intelligence, organizations can effectively stay on top of risks that could cut away at their revenues.
Editor’s Note: Jonathan Zhang is the founder and CEO of Threat Intelligence Platform (TIP)—a data, tool, and API provider that specializes in automated threat detection, security analysis, and threat intelligence solutions for Fortune 1000 and cybersecurity companies. TIP is part of the WhoisXML API family, a trusted intelligence vendor by over 50,000 clients.